Apps are listed in order of  "Highly Recommended" first, then
"Highly Recommended" first, then  "Worth a Try", then
"Worth a Try", then  "Not Recommended" last. Apps within the same recommendation level are ordered alphabetically.
"Not Recommended" last. Apps within the same recommendation level are ordered alphabetically.
Platforms: Android, iOS, MacOS, Windows
Communication types: Text, group chat, audio and video chat, photos, audio clips, files, location, contacts, screen sharing
Country of origin: Canada
Source code: closed
Encryption protocol: BlackBerry Certicom
Shared Secret exchange: ECDH P521
Message Encryption Cipher: AES-256
Business model: Subscriptions
Android app requires Google Play Services: Yes
Requires a phone number: No
Requires an email address: Yes
Your ID contains personal information: No
Data is locally encrypted: Yes
Encrypted by default: Yes
Perfect forward secrecy: Yes
Messages stored on server: Yes
Ephemeral messages: No
Puddle test: Data recoverable Messages are saved on the server
Hammer test: Data not recoverable When messages are deleted on both sending and receiving devices
Has contact verification: Yes
Leaks files: No
Android app trackers (2): Glympse, MixPanel
Websites: BBM Enterprise Security Note
Version tested: 1.12.1.13 (Android), 1.7.0.13 (iOS), 1.12.0.14 (MacOS)
Last tested: 4/3/2021
Notes:
4/3/2021- I updated BBMe to "highly recommended" because they recently removed Google tracking from the mobile apps.
[A big thank you to the cool cat (you know who you are) who helped me test BBMe and pointed out some things I missed.]
One of the giants and first to the secure messaging arena is BlackBerry Messenger. This app is now opening up it's enterprise application to everyone. This is great news for adoption of secure messaging:
https://www.techrepublic.com/article/blackberry-opens-bbm-enterprise-for-personal-use-after-emtek-discontinues-bbm-consumer/
I was very excited to try this app now that it is available without a corporate account. The new publicly available accounts will be free for the first year, then the fee is US $2.49 every 6 months. This is a very reasonable price for such an app.
If you use an alternate Android OS such as LineageOS and are trying to stay away from Google, BBMe could present some trouble for you in signing up. You need to have a Play Store account and a valid payment method setup in order to create a subscription. I ran into this problem because I don't use a personal Google account anymore. My solution was to instead sign up on an iPhone with my Apple Store account. Then once all setup on an iPhone you are able to install the app on Android and sign in with your BlackBerry Messenger PIN without needing to verify a payment method in the Play Store.
Data leakage (especially photos) prevented! BBMe gives you an option on whether it saves photos to your phone's photo gallery, or keeps them encrypted only in the BBMe database! I love that BBMe give me a choice!! I can turn this feature off, and be sure any photos in BBMe stay only in BBMe and are not leaked. Thank you! All other data is also saved encrypted on the device in a BBMe exclusive database.
BBMe does have "Timed messages" however these cannot really be considered "ephemeral" messages. These timed messages set a timer for the message to expire once they have been read by the recipient. However the timeout options are very short- only up to 60 seconds at most and the timeout period only begins once a message has been read. Therefore it is possible that a message is never read and it will never expire. Also this feature is reset upon every new message to be disabled, so it is not a feature that can be easily used to ensure every message will expire after it is read. With such a short timeout and no way to set this timeout as a permanent or always on feature the timeout is really only practical for the most sensitive messages. To me this feature isn't very useful except in rare circumstances so I can't set ephemeral messages as a listed feature of BBMe.
One feature I do really like is "Retractable" messages. Any message you send can be retracted and the message contents will be deleted from all recipient's devices if possible. There will still be a message remaining that just says "Message retracted" on the recipient's devices so there will be some meta data remaining that shows a message was sent. This remaining data can be deleted as well just like any other message but this is an additional step that must be done on each device. There is also an option to retract an entire chat. If you do this then create a new chat with your recipients then you are essentially forcing a complete key change for a conversation and deleting all history. This is a nice feature to have to be able to cleanup old conversations or easily keep the amount of data retained on devices very low.
There is a "Feeds" section in BBMe which will alert you when any of your contact's keys change. Each contact has a key fingerprint that you can compare in person or using another communication channel to verify the key you see matches the key on their device.
BBM is a mature product, so the chat session does have lots of useful features including quoting, editing and retracting your sent messages, deleting messages (on your device only), search, screenshot alerts, mentioning participants, and delivery and read receipts for every person in the chat. You can also use audio and video chat and on desktop versions do screen sharing. In the chat room details there are some notification options, sections which show all pictures, files and links from the chat grouped together, and a list of all room participants. Groups are able to have up to 250 participants at once.
If you are able to meet in person, there is a handy way to add a contact by scanning their QR code or through NFC. Otherwise you can add contacts by searching for their BlackBerry PIN, email or phone number.
This app is available for multiple platforms on mobile and desktop devices, so this makes it a great option for almost anyone to use. Messages are synced perfectly when you have this installed on multiple devices, and the interface experience is fairly consistant between the various operating system options. This versatility to use BBMe almost anywhere is an advantage over many other messengers.
My verdict: It has the security features you need, only a couple things I wish were better
Overall BlackBerry Messenger Enterprise is a great app with a solid history. The encryption is robust and the chat experience is very nice. For a centralized system it has the security features that are required to be a recommendation. I wish it had longer message timeouts and a way to set all messages to timeout by default. Also it would be very nice if there were a Linux client for the desktop.
Note that BlackBerry is based in Canada if you are concerned about 5 Eyes.
Communication types: Text, group chat, audio and video chat, photos, audio clips, files, location, contacts, screen sharing
Country of origin: Canada
Source code: closed
Encryption protocol: BlackBerry Certicom
Shared Secret exchange: ECDH P521
Message Encryption Cipher: AES-256
Business model: Subscriptions
Android app requires Google Play Services: Yes
Requires a phone number: No
Requires an email address: Yes
Your ID contains personal information: No
Data is locally encrypted: Yes
Encrypted by default: Yes
Perfect forward secrecy: Yes
Messages stored on server: Yes
Ephemeral messages: No
Puddle test: Data recoverable Messages are saved on the server
Hammer test: Data not recoverable When messages are deleted on both sending and receiving devices
Has contact verification: Yes
Leaks files: No
Android app trackers (2): Glympse, MixPanel
Websites: BBM Enterprise Security Note
Version tested: 1.12.1.13 (Android), 1.7.0.13 (iOS), 1.12.0.14 (MacOS)
Last tested: 4/3/2021
Notes:
4/3/2021- I updated BBMe to "highly recommended" because they recently removed Google tracking from the mobile apps.
[A big thank you to the cool cat (you know who you are) who helped me test BBMe and pointed out some things I missed.]
One of the giants and first to the secure messaging arena is BlackBerry Messenger. This app is now opening up it's enterprise application to everyone. This is great news for adoption of secure messaging:
https://www.techrepublic.com/article/blackberry-opens-bbm-enterprise-for-personal-use-after-emtek-discontinues-bbm-consumer/
I was very excited to try this app now that it is available without a corporate account. The new publicly available accounts will be free for the first year, then the fee is US $2.49 every 6 months. This is a very reasonable price for such an app.
If you use an alternate Android OS such as LineageOS and are trying to stay away from Google, BBMe could present some trouble for you in signing up. You need to have a Play Store account and a valid payment method setup in order to create a subscription. I ran into this problem because I don't use a personal Google account anymore. My solution was to instead sign up on an iPhone with my Apple Store account. Then once all setup on an iPhone you are able to install the app on Android and sign in with your BlackBerry Messenger PIN without needing to verify a payment method in the Play Store.
Data leakage (especially photos) prevented! BBMe gives you an option on whether it saves photos to your phone's photo gallery, or keeps them encrypted only in the BBMe database! I love that BBMe give me a choice!! I can turn this feature off, and be sure any photos in BBMe stay only in BBMe and are not leaked. Thank you! All other data is also saved encrypted on the device in a BBMe exclusive database.
BBMe does have "Timed messages" however these cannot really be considered "ephemeral" messages. These timed messages set a timer for the message to expire once they have been read by the recipient. However the timeout options are very short- only up to 60 seconds at most and the timeout period only begins once a message has been read. Therefore it is possible that a message is never read and it will never expire. Also this feature is reset upon every new message to be disabled, so it is not a feature that can be easily used to ensure every message will expire after it is read. With such a short timeout and no way to set this timeout as a permanent or always on feature the timeout is really only practical for the most sensitive messages. To me this feature isn't very useful except in rare circumstances so I can't set ephemeral messages as a listed feature of BBMe.
One feature I do really like is "Retractable" messages. Any message you send can be retracted and the message contents will be deleted from all recipient's devices if possible. There will still be a message remaining that just says "Message retracted" on the recipient's devices so there will be some meta data remaining that shows a message was sent. This remaining data can be deleted as well just like any other message but this is an additional step that must be done on each device. There is also an option to retract an entire chat. If you do this then create a new chat with your recipients then you are essentially forcing a complete key change for a conversation and deleting all history. This is a nice feature to have to be able to cleanup old conversations or easily keep the amount of data retained on devices very low.
There is a "Feeds" section in BBMe which will alert you when any of your contact's keys change. Each contact has a key fingerprint that you can compare in person or using another communication channel to verify the key you see matches the key on their device.
BBM is a mature product, so the chat session does have lots of useful features including quoting, editing and retracting your sent messages, deleting messages (on your device only), search, screenshot alerts, mentioning participants, and delivery and read receipts for every person in the chat. You can also use audio and video chat and on desktop versions do screen sharing. In the chat room details there are some notification options, sections which show all pictures, files and links from the chat grouped together, and a list of all room participants. Groups are able to have up to 250 participants at once.
If you are able to meet in person, there is a handy way to add a contact by scanning their QR code or through NFC. Otherwise you can add contacts by searching for their BlackBerry PIN, email or phone number.
This app is available for multiple platforms on mobile and desktop devices, so this makes it a great option for almost anyone to use. Messages are synced perfectly when you have this installed on multiple devices, and the interface experience is fairly consistant between the various operating system options. This versatility to use BBMe almost anywhere is an advantage over many other messengers.
My verdict: It has the security features you need, only a couple things I wish were better
Overall BlackBerry Messenger Enterprise is a great app with a solid history. The encryption is robust and the chat experience is very nice. For a centralized system it has the security features that are required to be a recommendation. I wish it had longer message timeouts and a way to set all messages to timeout by default. Also it would be very nice if there were a Linux client for the desktop.
Note that BlackBerry is based in Canada if you are concerned about 5 Eyes.
Platforms: Android
Communication types: Text, voice, video, files, images
Country of origin: USA
Source code: partialopen
Encryption protocol: Signal
Shared Secret exchange: X3DH Curve25519 or Curve448
Message Encryption Cipher: AES-256
Business model: Free open source project supported by donations
Android app requires Google Play Services: No
Requires a phone number: Yes
Requires an email address: No
Your ID contains personal information: Phone
Data is locally encrypted: Yes
Encrypted by default: Yes
Perfect forward secrecy: Yes
Messages stored on server: Temporarily
Ephemeral messages: Yes
Puddle test: Data not recoverable Messages saved only on device
Hammer test: Data not recoverable When messages are deleted on both sending and receiving devices
Has contact verification: Yes
Leaks files: No
Android app trackers (0): None
Websites: Source Code
Version tested: 5.26.11-1-FOSS
Last tested: 12/5/2021
Notes:
Molly is a fork of the Signal messenger app that adds a few more security features, removes the ability to send normal unencrypted SMS messages and also has a build that removes Google Firebase and Maps libraries. This alternative to Signal uses up to date source code from the official Signal clients so works in almost exacty the same way as the official application. If you already use Signal then creating a backup of your Signal data and importing it into Molly works perfectly.
One advantage I feel Molly has over Signal is that Molly removes the ability to send regular unencrypted SMS messages, thus making Molly a foolproof encrypted messenger. There is no way to mistakenly send an unencrypted message, because you can only send messages to other Signal/Molly users. This does mean that you will need to use a separate SMS app for regular SMS messages but I feel this should be the way people use SMS.
Molly also adds several security and privacy features such as:
Molly uses the Signal encryption protocol which is one of the best available right now. It takes advantage of the latest in elliptical curve cryptography, ratcheting, perfect forward secrecy, key fingerprints and ephemeral messages.
See my review on Signal for more details on how the core functionality of Molly stands up, since Molly os forked from Signal with some minor changes.
Encryption:
I'll let Signal explain this.
My verdict: Excellent alternative to Signal
If you already use Signal then this option may appeal to you if you wish to gain even more freedom from Google or don't like that Signal can also send unencrypted SMS messages. This apps works almost identical to Signal and is fully compatible with messaging to both Signal and Molly users.
Communication types: Text, voice, video, files, images
Country of origin: USA
Source code: partialopen
Encryption protocol: Signal
Shared Secret exchange: X3DH Curve25519 or Curve448
Message Encryption Cipher: AES-256
Business model: Free open source project supported by donations
Android app requires Google Play Services: No
Requires a phone number: Yes
Requires an email address: No
Your ID contains personal information: Phone
Data is locally encrypted: Yes
Encrypted by default: Yes
Perfect forward secrecy: Yes
Messages stored on server: Temporarily
Ephemeral messages: Yes
Puddle test: Data not recoverable Messages saved only on device
Hammer test: Data not recoverable When messages are deleted on both sending and receiving devices
Has contact verification: Yes
Leaks files: No
Android app trackers (0): None
Websites: Source Code
Version tested: 5.26.11-1-FOSS
Last tested: 12/5/2021
Notes:
Molly is a fork of the Signal messenger app that adds a few more security features, removes the ability to send normal unencrypted SMS messages and also has a build that removes Google Firebase and Maps libraries. This alternative to Signal uses up to date source code from the official Signal clients so works in almost exacty the same way as the official application. If you already use Signal then creating a backup of your Signal data and importing it into Molly works perfectly.
One advantage I feel Molly has over Signal is that Molly removes the ability to send regular unencrypted SMS messages, thus making Molly a foolproof encrypted messenger. There is no way to mistakenly send an unencrypted message, because you can only send messages to other Signal/Molly users. This does mean that you will need to use a separate SMS app for regular SMS messages but I feel this should be the way people use SMS.
Molly also adds several security and privacy features such as:
- Data encryption at rest - Protect the database with passphrase encryption
- Secure RAM wiper - Securely shred sensitive data from device memory
- Automatic lock - Lock the app automatically under certain conditions
- Block unknown contacts - Block messages and calls from unknown senders for security and anti-spam
- Contact deletion - Allows you to delete contacts and stop sharing your profile
- Disappearing call history - Clear call notifications together with expiring messages
- Debug logs are optional - Android logging can be disabled
- Custom backup scheduling - Choose between daily or weekly interval and the number of backups to retain
- SOCKS proxy and Tor support - Tunnel app network traffic via proxy and Orbot
Molly uses the Signal encryption protocol which is one of the best available right now. It takes advantage of the latest in elliptical curve cryptography, ratcheting, perfect forward secrecy, key fingerprints and ephemeral messages.
See my review on Signal for more details on how the core functionality of Molly stands up, since Molly os forked from Signal with some minor changes.
Encryption:
I'll let Signal explain this.
My verdict: Excellent alternative to Signal
If you already use Signal then this option may appeal to you if you wish to gain even more freedom from Google or don't like that Signal can also send unencrypted SMS messages. This apps works almost identical to Signal and is fully compatible with messaging to both Signal and Molly users.
Platforms: Android (Direct APK download), iOS, MacOS, Windows, Linux (Debian)
Communication types: Text, voice, video, files, images
Country of origin: USA
Source code: partialopen
Encryption protocol: Signal
Shared Secret exchange: X3DH Curve25519 or Curve448
Message Encryption Cipher: AES-256
Business model: Free open source project supported by grants and donations
Android app requires Google Play Services: No
Requires a phone number: Yes
Requires an email address: No
Your ID contains personal information: Phone
Data is locally encrypted: Yes
Encrypted by default: No
Perfect forward secrecy: Yes
Messages stored on server: Temporarily
Ephemeral messages: Yes
Puddle test: Data not recoverable Messages saved only on device
Hammer test: Data not recoverable When messages are deleted on both sending and receiving devices
Has contact verification: Yes
Leaks files: No
Android app trackers (0): None
Websites: Source Code, Technical docs
Version tested: 5.5.5
Last tested: 4/4/2021
Notes:
Signal is a great way to get started in the encrypted messaging world. It works very much like standard SMS messaging apps and also uses phone numbers of your contacts just like SMS does. When you do use encryption to send messages to other Signal users the encryption protocol used is one of the best available right now. It takes advantage of the latest in elliptical curve cryptography, ratcheting, perfect forward secrecy, key fingerprints and ephemeral messages.
One disadvantage of being similar to an SMS app however is the use of your phone number as your ID. This is a problem if you want to keep your phone number private.
More is Less: On the End-to-End Security of Group Chats in Signal, WhatsApp, and Threema
Encryption:
I'll let Signal explain this.
Whether Signal is fully open source is an open debate. The Github repo for the server does not seem to be up to date, and other pieces of the system such as the new SGX contacts isolation is not available. So I am marking this partially open for now.
My verdict: Best SMS replacement app
This app may be the easiest to convince other people to use. However it requires the use of your phone number as an identifier, so if you are not comfortable giving some people your phone number there are better options to communicate with them. See my Signal Installation Guide for details on getting started with this app.
Communication types: Text, voice, video, files, images
Country of origin: USA
Source code: partialopen
Encryption protocol: Signal
Shared Secret exchange: X3DH Curve25519 or Curve448
Message Encryption Cipher: AES-256
Business model: Free open source project supported by grants and donations
Android app requires Google Play Services: No
Requires a phone number: Yes
Requires an email address: No
Your ID contains personal information: Phone
Data is locally encrypted: Yes
Encrypted by default: No
Perfect forward secrecy: Yes
Messages stored on server: Temporarily
Ephemeral messages: Yes
Puddle test: Data not recoverable Messages saved only on device
Hammer test: Data not recoverable When messages are deleted on both sending and receiving devices
Has contact verification: Yes
Leaks files: No
Android app trackers (0): None
Websites: Source Code, Technical docs
Version tested: 5.5.5
Last tested: 4/4/2021
Notes:
Signal is a great way to get started in the encrypted messaging world. It works very much like standard SMS messaging apps and also uses phone numbers of your contacts just like SMS does. When you do use encryption to send messages to other Signal users the encryption protocol used is one of the best available right now. It takes advantage of the latest in elliptical curve cryptography, ratcheting, perfect forward secrecy, key fingerprints and ephemeral messages.
One disadvantage of being similar to an SMS app however is the use of your phone number as your ID. This is a problem if you want to keep your phone number private.
Signal is not Foolproof:
Another issue with this app is that both encrypted Signal messages and unencrypted SMS messages are displayed on a single screen in the app. So there is a chance of accidentally sending an unencrypted message when you really meant to send an encrypted message. If you are trying to avoid the possibility of mistakenly sending any messages unencrypted then this app will not work for you.[Information provided by JR]
What the server sees:
- The phone number used for your registration.
- SHA-2 Hashes of your contacts' telephone numbers to check for a match. OWS claims to delete this as soon as it is no longer needed.
What Signal claims to keep:
- The day you first joined the service
- The last day you used it.
Disadvantages:
- People must know your phone number. It is possible to register a burner number or a VOIP number, but this is an advanced-use case.
More is Less: On the End-to-End Security of Group Chats in Signal, WhatsApp, and Threema
Encryption:
I'll let Signal explain this.
Whether Signal is fully open source is an open debate. The Github repo for the server does not seem to be up to date, and other pieces of the system such as the new SGX contacts isolation is not available. So I am marking this partially open for now.
My verdict: Best SMS replacement app
This app may be the easiest to convince other people to use. However it requires the use of your phone number as an identifier, so if you are not comfortable giving some people your phone number there are better options to communicate with them. See my Signal Installation Guide for details on getting started with this app.
Platforms: Android (Threema Shop), iOS, Web
Communication types: Text, group chat, voice, files, voice chat
Country of origin: Switzerland
Source code: partialopen
Encryption protocol: NaCl
Shared Secret exchange: ECDH25519
Message Encryption Cipher: XSalsa20
Business model: One time app purchase fee
Android app requires Google Play Services: No
Requires a phone number: No
Requires an email address: No
Your ID contains personal information: No
Data is locally encrypted: Yes
Encrypted by default: Yes
Perfect forward secrecy: No
Messages stored on server: Temporarily
Ephemeral messages: No
Puddle test: Data not recoverable Messages are saved on the device only.
Hammer test: Data not recoverable When messages are deleted on all devices.
Has contact verification: Yes
Leaks files: No
Android app trackers (1): Mapbox
Websites: Cryptography Whitepaper, Audit (2019), Audit (2020), Open source info
Version tested: 4.52
Last tested: 4/4/2021
Notes:
Threema is very easy to setup and use. Linking to an email or phone number is totally optional. To add a contact you need to acquire their Threema ID via a separate channel, search your contacts list for a match, or scan their fingerprint QR code in person. These three methods attach 3 levels of "verification" to your contacts:
It is also very easy to create encrypted group chats with multiple contacts. All individual and group chats will show up in the same list.
Search feature in individual and group chats.
Threema is partially open source
From the FAQ:
More is Less: On the End-to-End Security of Group Chats in Signal, WhatsApp, and Threema
Encryption process (from the whitepaper):
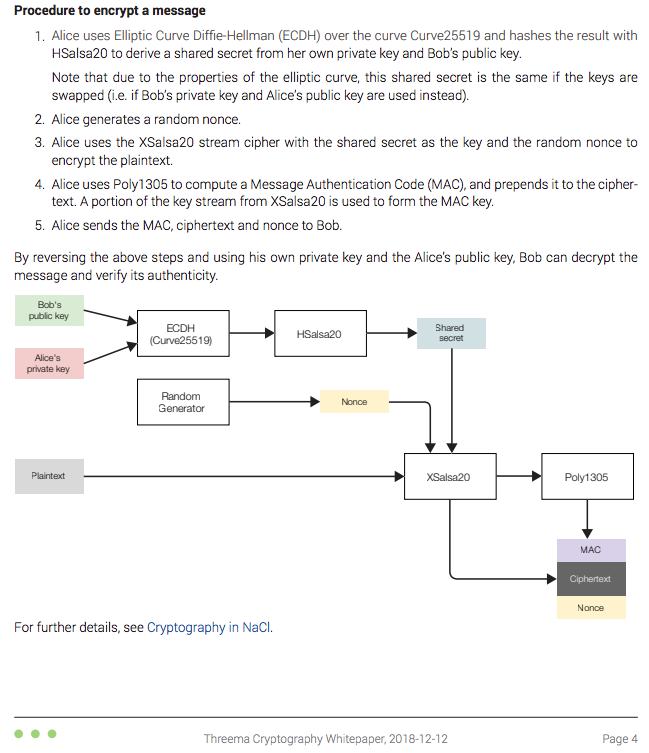
This process uses the Box model of the NaCl cryptography library.
A shared secret is generated using both the private key of one chat participant and the public key of the other participant. So both participants are able to generate the same shared secret without the need for any negotiations over the internet or transmitting any information at all, except for initially acquiring the other participant's public key. This also has the advantage of being able to generate the secret while the other participant is offline. This shared secret cannot change, unless one of the participants changes their Threema ID (and thus their key pair).
Each message has a random nonce generated for it, this acts as a salt value, and is combined with the shared secret to encrypt the message. This does not provide perfect forward secrecy, but it does insert an element of randomness so that analysis of Threema encrypted messages is made more difficult than a series of messages encrypted with Public Key Infrastructure methods that use the same symmetric key for every message.
For group chats when a message is send the message is encrypted separately for every member of the group using the same method as a one to one chat. So if there are 12 participants in a group, a message will be encrypted 11 times, once for each of the other group members, and each message will have a different nonce.
This looks interesting- an open source implimentation of the Threema client (not official): openMittsu
My Verdict: Almost perfect
Truly this is an app that provides almost a perfect secured messaging system. Limited meta data, very easy to use, foolproof encryption. The only features missing are perfect forward secrecy on message encryption (data in transit is additionally encrypted with TLS) and ephemeral messages. Oh and being able to use it on multiple devices would be nice as well. But the simplicity of use and low cost are what make this app a top choice for me.
Communication types: Text, group chat, voice, files, voice chat
Country of origin: Switzerland
Source code: partialopen
Encryption protocol: NaCl
Shared Secret exchange: ECDH25519
Message Encryption Cipher: XSalsa20
Business model: One time app purchase fee
Android app requires Google Play Services: No
Requires a phone number: No
Requires an email address: No
Your ID contains personal information: No
Data is locally encrypted: Yes
Encrypted by default: Yes
Perfect forward secrecy: No
Messages stored on server: Temporarily
Ephemeral messages: No
Puddle test: Data not recoverable Messages are saved on the device only.
Hammer test: Data not recoverable When messages are deleted on all devices.
Has contact verification: Yes
Leaks files: No
Android app trackers (1): Mapbox
Websites: Cryptography Whitepaper, Audit (2019), Audit (2020), Open source info
Version tested: 4.52
Last tested: 4/4/2021
Notes:
Threema is very easy to setup and use. Linking to an email or phone number is totally optional. To add a contact you need to acquire their Threema ID via a separate channel, search your contacts list for a match, or scan their fingerprint QR code in person. These three methods attach 3 levels of "verification" to your contacts:
- Red- Anonymous (added manually)
- Yellow- Matches a contact in your address book
- Green- QR code scanned in person
It is also very easy to create encrypted group chats with multiple contacts. All individual and group chats will show up in the same list.
Search feature in individual and group chats.
Threema is partially open source
From the FAQ:
Which data gets stored at Threema?
Using Threema ought to generate as little data on servers as possible – this is part of the concept. For that reason, data like e.g. contacts or group chats are stored in a decentralized way on user devices, instead of on a Threema server. Our servers assume the role of a switch; messages and data get forwarded, but not permanently stored. Where there is no data, there is nothing to be accessed or misused. However: without some kind of (temporary) data storage, there cannot be any asynchronous communication. In the following we will explain what kind of data we store, how we store it and for how long.
Messages and group chats: As soon as a message has been successfully delivered to the recipient, it is immediately deleted from the server. All messages and media are transmitted end-to-end encrypted in Threema. This means: even if someone intercepted your message, it would be completely useless. Only the intended recipient is able to decrypt and read a message.
No contact lists are stored when synchronizing contacts: The email addresses and phone numbers from your address book get anonymized (hashed) before they reach the server. Once the comparison is finished, they are immediately deleted from the server.
Key pairs are generated in a decentralized way on your device. Your private key is never known to us, and therefore we cannot decrypt any message contents.
Threema doesn't log who is communicating with whom (which Threema IDs are communicating).
More is Less: On the End-to-End Security of Group Chats in Signal, WhatsApp, and Threema
Encryption process (from the whitepaper):

This process uses the Box model of the NaCl cryptography library.
A shared secret is generated using both the private key of one chat participant and the public key of the other participant. So both participants are able to generate the same shared secret without the need for any negotiations over the internet or transmitting any information at all, except for initially acquiring the other participant's public key. This also has the advantage of being able to generate the secret while the other participant is offline. This shared secret cannot change, unless one of the participants changes their Threema ID (and thus their key pair).
Each message has a random nonce generated for it, this acts as a salt value, and is combined with the shared secret to encrypt the message. This does not provide perfect forward secrecy, but it does insert an element of randomness so that analysis of Threema encrypted messages is made more difficult than a series of messages encrypted with Public Key Infrastructure methods that use the same symmetric key for every message.
For group chats when a message is send the message is encrypted separately for every member of the group using the same method as a one to one chat. So if there are 12 participants in a group, a message will be encrypted 11 times, once for each of the other group members, and each message will have a different nonce.
This looks interesting- an open source implimentation of the Threema client (not official): openMittsu
My Verdict: Almost perfect
Truly this is an app that provides almost a perfect secured messaging system. Limited meta data, very easy to use, foolproof encryption. The only features missing are perfect forward secrecy on message encryption (data in transit is additionally encrypted with TLS) and ephemeral messages. Oh and being able to use it on multiple devices would be nice as well. But the simplicity of use and low cost are what make this app a top choice for me.
Platforms: Android, iOS
Communication types: Text, group chat, files, photos, voice, video, location
Country of origin: Singapore
Source code: closed
Encryption protocol: ?
Shared Secret exchange: ECDH25519
Message Encryption Cipher: AES-256
Business model:
Android app requires Google Play Services: Yes
Requires a phone number: No
Requires an email address: No
Your ID contains personal information: No
Data is locally encrypted: Yes
Encrypted by default: Yes
Perfect forward secrecy: Yes
Messages stored on server: Temporarily
Ephemeral messages: Yes
Puddle test: Data not recoverable Messages are saved on the device only.
Hammer test: Data not recoverable When messages are deleted on all devices.
Has contact verification: No
Leaks files: No
Android app trackers (0): None
Websites: Security, FAQ
Version tested: 3.4.0
Last tested: 12/28/2019
Notes:
This app seems to be very well done, there were no issues encountered during testing. You can send just about any type of file, and there are nice features such as timed messages, quoting messages, read receipts and message retraction.
There isn't much info about the company behind this but they say they are based in Singapore. There are not trackers found in the Android app which is nice.
My verdict: Try it out, not sure of company origins
Very feature complete and very fast sending messages.
Communication types: Text, group chat, files, photos, voice, video, location
Country of origin: Singapore
Source code: closed
Encryption protocol: ?
Shared Secret exchange: ECDH25519
Message Encryption Cipher: AES-256
Business model:
Android app requires Google Play Services: Yes
Requires a phone number: No
Requires an email address: No
Your ID contains personal information: No
Data is locally encrypted: Yes
Encrypted by default: Yes
Perfect forward secrecy: Yes
Messages stored on server: Temporarily
Ephemeral messages: Yes
Puddle test: Data not recoverable Messages are saved on the device only.
Hammer test: Data not recoverable When messages are deleted on all devices.
Has contact verification: No
Leaks files: No
Android app trackers (0): None
Websites: Security, FAQ
Version tested: 3.4.0
Last tested: 12/28/2019
Notes:
This app seems to be very well done, there were no issues encountered during testing. You can send just about any type of file, and there are nice features such as timed messages, quoting messages, read receipts and message retraction.
There isn't much info about the company behind this but they say they are based in Singapore. There are not trackers found in the Android app which is nice.
My verdict: Try it out, not sure of company origins
Very feature complete and very fast sending messages.
Platforms: Android, iOS, MacOS, Windows, Linux (many)
Communication types: Text, group chat, files, voice, video, location
Country of origin: Bulgaria
Source code: closed
Encryption protocol: ?
Shared Secret exchange: ?
Message Encryption Cipher: AES-256
Business model: Enterprise version of the platform
Android app requires Google Play Services: No
Requires a phone number: No
Requires an email address: Yes
Your ID contains personal information: No
Data is locally encrypted: ?
Encrypted by default: Yes
Perfect forward secrecy: Yes
Messages stored on server: Temporarily
Ephemeral messages: No
Puddle test: Data not recoverable Messages are saved on the device only.
Hammer test: Data not recoverable There does not seem to be any way to delete messages or your account. The only way to really delete your messages is to uninstall the app.
Has contact verification: No
Leaks files: No
Android app trackers (0): None
Websites: Security
Version tested: 4.0.94
Last tested: 12/19/2018
Notes:
From the website:
Peer-to-Peer Connections – All communication channels between users are preferably peer-to-peer. If a direct connection is unable to be made, the communication passes through a tunnel server. With this, the sender encrypts the data with the recipient decrypting. Also, it’s important to note that the tunnel server never sees the data, never processes the data, and never stores the data.
This application was recently updated with a much improved user interface and usability. Sending text and pictures worked great and the location feature integrates nicely with the default Maps application on Android. If you have the Maps app disabled however the app will crash if you try to open a location marker in the app.
Brosix used to support connections to AIM, Google Talk and ICQ, however that is being dropped as of April 1, 2019 (probably a good thing).
My verdict: Definitely worth a try, much improved this year!
What I like is a much cleaner interface since the last version, the company is based outside the 14 eyes countries and it has a desktop application. It is still missing some security features like ephemeral messages and contact verification. It does get a bonus for not having any tracker libraries.
Communication types: Text, group chat, files, voice, video, location
Country of origin: Bulgaria
Source code: closed
Encryption protocol: ?
Shared Secret exchange: ?
Message Encryption Cipher: AES-256
Business model: Enterprise version of the platform
Android app requires Google Play Services: No
Requires a phone number: No
Requires an email address: Yes
Your ID contains personal information: No
Data is locally encrypted: ?
Encrypted by default: Yes
Perfect forward secrecy: Yes
Messages stored on server: Temporarily
Ephemeral messages: No
Puddle test: Data not recoverable Messages are saved on the device only.
Hammer test: Data not recoverable There does not seem to be any way to delete messages or your account. The only way to really delete your messages is to uninstall the app.
Has contact verification: No
Leaks files: No
Android app trackers (0): None
Websites: Security
Version tested: 4.0.94
Last tested: 12/19/2018
Notes:
From the website:
Peer-to-Peer Connections – All communication channels between users are preferably peer-to-peer. If a direct connection is unable to be made, the communication passes through a tunnel server. With this, the sender encrypts the data with the recipient decrypting. Also, it’s important to note that the tunnel server never sees the data, never processes the data, and never stores the data.
This application was recently updated with a much improved user interface and usability. Sending text and pictures worked great and the location feature integrates nicely with the default Maps application on Android. If you have the Maps app disabled however the app will crash if you try to open a location marker in the app.
Brosix used to support connections to AIM, Google Talk and ICQ, however that is being dropped as of April 1, 2019 (probably a good thing).
My verdict: Definitely worth a try, much improved this year!
What I like is a much cleaner interface since the last version, the company is based outside the 14 eyes countries and it has a desktop application. It is still missing some security features like ephemeral messages and contact verification. It does get a bonus for not having any tracker libraries.
Platforms: Android, iOS
Communication types: text, voice call, photos, contacts, location
Country of origin: USA
Source code: closed
Encryption protocol: Anonyome Cloud Platform
Shared Secret exchange: RSA 2048 PKI
Message Encryption Cipher: AES-256
Business model: Monthly subscription fee
Android app requires Google Play Services: N/A
Requires a phone number: No
Requires an email address: No
Your ID contains personal information: No
Data is locally encrypted: Yes
Encrypted by default: Yes for MySudo contacts, No for SMS
Perfect forward secrecy: ?
Messages stored on server: Yes
Ephemeral messages: Yes for MySudo contacts, No for SMS
Puddle test: Data recoverable Messages are saved on the server.
Hammer test: Data not recoverable When messages are deleted on all devices.
Has contact verification: No
Leaks files: No
Websites: Security Features
Version tested: 0.9.4
Last tested: 6/26/2018
Notes:
MySudo is an application that gives you a phone number (US or Canada) for calls or SMS and an email address. The phone number works just like your cell phone number but works over wifi. This is a really easy way to give yourself a second number to provide to any person or company you don't want to give your real number to. Or you can subscribe to a monthly plan and get multiple numbers and assign each number a role to seperate uses for each number. It is up to you to decide what the purpose of each number is.
So the end to end message encryption covers only other MySudo users you connect with. Anyone else uses regular SMS messages. So as a secure messaging platform, it is very similar to Signal, except that you are using what is essentially a VoIP phone number. However unless there is a large uptake in MySudo users, you may not have many opportunities to use E2EE messaging.
Currently is it for iOS only, however that may change inthe future.
My verdict: Great if you want a second phone number!
The main purpose of this app is to provide you with a second phone number that you can use instead of your primary cell phone number. The added functionality of E2EE (limited only to other iOS MySudo users) is really just a bonus. This will not replace you current messaging app anytime soon. There is nothing wrong with the app, it works very well for its intended purpose, which does not happen to be to take over the messaging universe.
Communication types: text, voice call, photos, contacts, location
Country of origin: USA
Source code: closed
Encryption protocol: Anonyome Cloud Platform
Shared Secret exchange: RSA 2048 PKI
Message Encryption Cipher: AES-256
Business model: Monthly subscription fee
Android app requires Google Play Services: N/A
Requires a phone number: No
Requires an email address: No
Your ID contains personal information: No
Data is locally encrypted: Yes
Encrypted by default: Yes for MySudo contacts, No for SMS
Perfect forward secrecy: ?
Messages stored on server: Yes
Ephemeral messages: Yes for MySudo contacts, No for SMS
Puddle test: Data recoverable Messages are saved on the server.
Hammer test: Data not recoverable When messages are deleted on all devices.
Has contact verification: No
Leaks files: No
Websites: Security Features
Version tested: 0.9.4
Last tested: 6/26/2018
Notes:
MySudo is an application that gives you a phone number (US or Canada) for calls or SMS and an email address. The phone number works just like your cell phone number but works over wifi. This is a really easy way to give yourself a second number to provide to any person or company you don't want to give your real number to. Or you can subscribe to a monthly plan and get multiple numbers and assign each number a role to seperate uses for each number. It is up to you to decide what the purpose of each number is.
So the end to end message encryption covers only other MySudo users you connect with. Anyone else uses regular SMS messages. So as a secure messaging platform, it is very similar to Signal, except that you are using what is essentially a VoIP phone number. However unless there is a large uptake in MySudo users, you may not have many opportunities to use E2EE messaging.
Currently is it for iOS only, however that may change inthe future.
My verdict: Great if you want a second phone number!
The main purpose of this app is to provide you with a second phone number that you can use instead of your primary cell phone number. The added functionality of E2EE (limited only to other iOS MySudo users) is really just a bonus. This will not replace you current messaging app anytime soon. There is nothing wrong with the app, it works very well for its intended purpose, which does not happen to be to take over the messaging universe.
Platforms: Linux, MacOS, Windows, Android
Communication types: Text
Country of origin: None
Source code: open
Encryption protocol: Tor hidden services/TLS
Shared Secret exchange: ECDH25519
Message Encryption Cipher: AES-128 or better
Business model: Free open source project
Android app requires Google Play Services: No
Requires a phone number: No
Requires an email address: No
Your ID contains personal information: No
Data is locally encrypted: Yes
Encrypted by default: Yes
Perfect forward secrecy: Yes
Messages stored on server: false
Ephemeral messages: Yes
Puddle test: Data not recoverable
Hammer test: Data not recoverable
Has contact verification: No
Leaks files: No
Websites: Source
Version tested: 2.3.2
Last tested: 8/5/2021
Notes:
OnionShare is a desktop application that offers an easy way to create servers for hosting websites, file sharing, file drop and chatting. All servers are accessible through a Tor .onion address so inherit all the security and privacy features of the Tor network.
The chat features are fairly basic at this time. It is text only and there are no notifications when new messages arrive. You also must have an active connection to the server to receive messages. If you are offline any messages sent to the server do not get delivered to you. As a consequence there is no history of saved messages that can be retrieved while you were offline.
The OnionShare application creates the server part of the chat system. This is very easy to do, you do not need to have any server administration experience or do any complicated systems setup. Just run the OnionShare application, choose a few settings and start the server on your own home computer. The server will have a .onion URL that you can send to anyone you want to connect to the chat server. To send and receive messages the "client" part of the chat system is actually the Tor Browser. Paste the .onion URL into the Tor Browser address bar and you are now connected to the chat server as a new user. There is no need to register accounts on the system, if you have the URL you can just connect to it. When first connected you are given a random name, which can be changed. By using the Tor browser this also makes it very easy for anyone to join the chat (as long as they have the URL) and the only requirement is to have the Tor Browser installed.
The Tor Browser on Android does also work as a client, however at the time of this review the interface is still scaled the same as when using the desktop Tor Browser, so the text is very small. But it is still usable. Also on Android when switching to another application the connection between Tor Browser and the OnionShare chat server is stopped, so if any messages are sent when you are not actively in Tor Browser these messages will not appear when you return to the Tor Browser. The desktop Tor Browsers do keep an active connection even when using other applications so as long as the tab is not closed you can receive messages from OnionShare while using other applications on a desktop.
No messages are stored anywhere to disk on either the server or client sides. You send a message to the server, and the server immmediately sends out that message only to those clients with an active connection. There is no history saved anywhere. The clients are really just a tab in the Tor Browser, so as soon as that tab is closed all the data and messages from the chat session are gone. These messages are therefore ephemeral as they are destroyed as soon as the clients are closed.
Because you must have an active connection to send/receive messages I see this chat system is best when used for short communcations when you really need privacy and ephemeral messages. You can quickly create a new chat server if you are communicating on another platform but feel the need for more privacy and security. This isn't really a system you would leave up running all the time. There are no notifications (yet) so you must manually check the Tor Browser tab for any new messages. Also if someone goes offline there is no way to queue a message for them to receive when they return. So this is really a system for when all parties in a conversation can be actively online at the same time.
The only other real downside to this system I can find is that there really isn't any type of contact verification. When someone connects they can put in any name for themselves that they want. So having a second scure channel of communication is important to send the URL to the chat server and verify that the person you wanted to connect is truely the one connected (verify the name they used).
My verdict: Excellent option when you want a private ad-hoc conversation
All participants must be actively online since all messages are transferred in real time without any queues. The server is very easy to setup (and take down) on a regular desktop PC, and the Tor Browser is the only requirement needed to connect to the server. All messages are destroyed as soon as the Tor Browser tab for the chat is closed.
Communication types: Text
Country of origin: None
Source code: open
Encryption protocol: Tor hidden services/TLS
Shared Secret exchange: ECDH25519
Message Encryption Cipher: AES-128 or better
Business model: Free open source project
Android app requires Google Play Services: No
Requires a phone number: No
Requires an email address: No
Your ID contains personal information: No
Data is locally encrypted: Yes
Encrypted by default: Yes
Perfect forward secrecy: Yes
Messages stored on server: false
Ephemeral messages: Yes
Puddle test: Data not recoverable
Hammer test: Data not recoverable
Has contact verification: No
Leaks files: No
Websites: Source
Version tested: 2.3.2
Last tested: 8/5/2021
Notes:
OnionShare is a desktop application that offers an easy way to create servers for hosting websites, file sharing, file drop and chatting. All servers are accessible through a Tor .onion address so inherit all the security and privacy features of the Tor network.
The chat features are fairly basic at this time. It is text only and there are no notifications when new messages arrive. You also must have an active connection to the server to receive messages. If you are offline any messages sent to the server do not get delivered to you. As a consequence there is no history of saved messages that can be retrieved while you were offline.
The OnionShare application creates the server part of the chat system. This is very easy to do, you do not need to have any server administration experience or do any complicated systems setup. Just run the OnionShare application, choose a few settings and start the server on your own home computer. The server will have a .onion URL that you can send to anyone you want to connect to the chat server. To send and receive messages the "client" part of the chat system is actually the Tor Browser. Paste the .onion URL into the Tor Browser address bar and you are now connected to the chat server as a new user. There is no need to register accounts on the system, if you have the URL you can just connect to it. When first connected you are given a random name, which can be changed. By using the Tor browser this also makes it very easy for anyone to join the chat (as long as they have the URL) and the only requirement is to have the Tor Browser installed.
The Tor Browser on Android does also work as a client, however at the time of this review the interface is still scaled the same as when using the desktop Tor Browser, so the text is very small. But it is still usable. Also on Android when switching to another application the connection between Tor Browser and the OnionShare chat server is stopped, so if any messages are sent when you are not actively in Tor Browser these messages will not appear when you return to the Tor Browser. The desktop Tor Browsers do keep an active connection even when using other applications so as long as the tab is not closed you can receive messages from OnionShare while using other applications on a desktop.
No messages are stored anywhere to disk on either the server or client sides. You send a message to the server, and the server immmediately sends out that message only to those clients with an active connection. There is no history saved anywhere. The clients are really just a tab in the Tor Browser, so as soon as that tab is closed all the data and messages from the chat session are gone. These messages are therefore ephemeral as they are destroyed as soon as the clients are closed.
Because you must have an active connection to send/receive messages I see this chat system is best when used for short communcations when you really need privacy and ephemeral messages. You can quickly create a new chat server if you are communicating on another platform but feel the need for more privacy and security. This isn't really a system you would leave up running all the time. There are no notifications (yet) so you must manually check the Tor Browser tab for any new messages. Also if someone goes offline there is no way to queue a message for them to receive when they return. So this is really a system for when all parties in a conversation can be actively online at the same time.
The only other real downside to this system I can find is that there really isn't any type of contact verification. When someone connects they can put in any name for themselves that they want. So having a second scure channel of communication is important to send the URL to the chat server and verify that the person you wanted to connect is truely the one connected (verify the name they used).
My verdict: Excellent option when you want a private ad-hoc conversation
All participants must be actively online since all messages are transferred in real time without any queues. The server is very easy to setup (and take down) on a regular desktop PC, and the Tor Browser is the only requirement needed to connect to the server. All messages are destroyed as soon as the Tor Browser tab for the chat is closed.
Platforms: Android, iOS, Windows
Communication types: Text, group chat, voice, pictures, video, location
Country of origin: Switzerland
Source code: closed
Encryption protocol: NaCl
Shared Secret exchange: ECDH25519
Message Encryption Cipher: XSalsa20
Business model: Digital communication security solutions
Android app requires Google Play Services: No
Requires a phone number: No
Requires an email address: No
Your ID contains personal information: No
Data is locally encrypted: Yes
Encrypted by default: Yes
Perfect forward secrecy: Yes
Messages stored on server: Never
Ephemeral messages: Yes
Puddle test: Data not recoverable Messages saved only on device
Hammer test: Data not recoverable When messages are deleted on both sending and receiving devices
Has contact verification: Yes
Leaks files: No
Android app trackers (3): Google CrashLytics, Google Firebase Analytics, HockeyApp
Websites: Encryption
Version tested: 1.4.20
Last tested: 12/5/2019
Notes:
Registering your email or phone number is optional.
Messages are saved (encrypted) on the server if the recipient is not online, delivered and erased once they are online.
Self destruct messages, perfect forward secrecy
Encryption process (from the FAQ):
SafeSwiss uses the Box model of the NaCl Networking and Cryptography Library.
The shared secrets, which are used as symmetric keys for end-to-end message encryption (derived from the sender’s private key and the recipient’s public key using ECDH, and combined with a 192 bit nonce), have a length of 256 bits.
A unique session key is generated for each communication, which is used as input to the NaCl Box function to generate the encryption key. Thus SafeSwiss is able to create ephemeral messages that have perfect forward secrecy.
Communication types: Text, group chat, voice, pictures, video, location
Country of origin: Switzerland
Source code: closed
Encryption protocol: NaCl
Shared Secret exchange: ECDH25519
Message Encryption Cipher: XSalsa20
Business model: Digital communication security solutions
Android app requires Google Play Services: No
Requires a phone number: No
Requires an email address: No
Your ID contains personal information: No
Data is locally encrypted: Yes
Encrypted by default: Yes
Perfect forward secrecy: Yes
Messages stored on server: Never
Ephemeral messages: Yes
Puddle test: Data not recoverable Messages saved only on device
Hammer test: Data not recoverable When messages are deleted on both sending and receiving devices
Has contact verification: Yes
Leaks files: No
Android app trackers (3): Google CrashLytics, Google Firebase Analytics, HockeyApp
Websites: Encryption
Version tested: 1.4.20
Last tested: 12/5/2019
Notes:
Registering your email or phone number is optional.
Messages are saved (encrypted) on the server if the recipient is not online, delivered and erased once they are online.
Self destruct messages, perfect forward secrecy
Encryption process (from the FAQ):
SafeSwiss uses the Box model of the NaCl Networking and Cryptography Library.
- Diffie-Hellman key exchange using Curve25519
- These keys are hashed to derive a shared secret
- The shared secret is combined with a unique nonce to encrypt the message
- Poly1305 is used to create a message authentication code
The shared secrets, which are used as symmetric keys for end-to-end message encryption (derived from the sender’s private key and the recipient’s public key using ECDH, and combined with a 192 bit nonce), have a length of 256 bits.
A unique session key is generated for each communication, which is used as input to the NaCl Box function to generate the encryption key. Thus SafeSwiss is able to create ephemeral messages that have perfect forward secrecy.
Platforms: Android, iOS, MacOS, Windows, Linux (Snap)
Communication types: Text, group chat, videos, files, audio message, voice calls
Country of origin: USA
Source code: partialopen
Encryption protocol: Wickr Messaging Protocol
Shared Secret exchange: ECDH P521
Message Encryption Cipher: AES-256
Business model: Enterprise version of the platform
Android app requires Google Play Services: No
Requires a phone number: No
Requires an email address: No
Your ID contains personal information: No
Data is locally encrypted: Yes
Encrypted by default: Yes
Perfect forward secrecy: Yes
Messages stored on server: Temporarily
Ephemeral messages: Yes
Puddle test: Data not recoverable Messages not saved on the server, only on each device. Contacts are recovered.
Hammer test: Data not recoverable Every message is ephemeral, chats can be manually deleted.
Has contact verification: Yes
Leaks files: No
Android app trackers (3): Bugsnag, Countly, Google Firebase Analytics
Websites: Secure Messaging Protocol source
Version tested: 4.62.0
Last tested: 10/30/2018
Notes:
June 2021- Amazon acquires Wickr to add to its AWS service offerings: https://www.slashgear.com/amazon-buys-wickr-a-secure-messaging-platform-even-the-nsa-likes-25679984/. This looks like a way to secure future contracts with the US Govt.
Partially open source (cypto protocol only)
1/24/2020- Received FIPs certification for crypto module
WickrMe synchronizes your chats across all your devices. Actually what happens is there is a separate message encrypted for each registered device you have. So if any devices are offline, those messages will be stored temporarily on the server until the device is online and is able to retrieve the message. Messages are stored for up to 6 days, after which they expire and are deleted from the server.
All messages expire, with the timeout beginning once the message has been read. You can choose a timeout of up to 6 days. This is a nice feature that you can have peace of mind that all messages will be deleted.
The desktop clients work very well and make it easy to transition between messaging on a mobile devices and doing so on a desktop. It is available for all major platforms including Ubuntu Linux.
There are not many unique features, but as a basic chat client it works very well. It has video chat (I haven't tried that yet), audio messages and file transfers. Notifications are reliable even on Lineage for MicroG.
Encryption process (from the wiki):
Each device that a WickrMe user uses is considered a node with it's own set of encryption keys. Each node creates a pool of asymmetric Diffie-Hellman public key pairs and sends the public keys to the WickrMe server. These are available for other nodes to use for sending messages.
When sending a message, a copy of the encrypted message packet is sent to all of the nodes of the recipient, plus to all the other nodes of the sender so that all the sender's devices also remain in sync. Every node receives an exact copy of the same message bundle, it is packaged so that all recipient nodes can decrypt the same message bundle.
One random symmetric key is generated which encrypts the actual message data. Then a new public key pair is generated on the sender's device to use once for this message bundle. One public key is retrieved from the pool of each node that will receive the message. The sender node's private key and each one of the repient nodes' public key is used to encrypt the symmetric message encryption key. So there will be N copies of the symmetric key encrypted and included in the message bundle. Then the encrypted message data, all the encrypted copies of the symmetric key and the public key of the sender's node is packaged together into the final message bundle which is sent to all the recipient nodes.
So one important question with this model, is it a risk having data (in this instance it happens to be the symmetric message encryption key) encrypted multiple times with different key pairs for each recipient and having all those copies included with the message bundle for all other recipents to access? If one node receives encrypted data intended for all the other nodes, encrypted with their keys, doesn't that expose a risk that one node could break the private key used by another node? The answer is yes that is a theoretical risk, but not a practical one. The reason is that each public key used to encrypt the actual message encryption key is only ever used once then destroyed. So yes having a known piece of data encrypted with multiple keys does make it theoretically easier to break any of the other secret keys needed to decrypt the message. However, this message was also sent to you, so you already know the contents of this message! Nothing is revealed that you do not already know. And since any private keys you may discover are never used again, they cannot be used to decrypt any other messages. (Note, I sent a question to Wickr and confirmed with them that in fact each public/private key pair between nodes is only used one time and discarded.)
My verdict: One of the very best, however concerns about country jurisdiction and trackers and ownership!
This app has a complete set of security features, and is practically "foolproof", by which I mean you can just use it and not worry about doing something that will compromise the security of your messages. At most your messages will sit around on your chat partners device or the WickrMe server (encrypted of course) for 6 days before being automatically deleted. Also it requires no personal information making it very anonymous. It does what it is supposed to do simply without a lot of flash.
The only downside is that the system is owned by Amazon and based in the USA (part of the 5 eyes) and I usually stay away from any messaging apps with servers there. However I am very confident in the security and anonymity of the system so this is one of the few messengers based in the US that I do use. You can also see their transparency report. The three trackers in the app are more than I would prefer it to have as well.
Communication types: Text, group chat, videos, files, audio message, voice calls
Country of origin: USA
Source code: partialopen
Encryption protocol: Wickr Messaging Protocol
Shared Secret exchange: ECDH P521
Message Encryption Cipher: AES-256
Business model: Enterprise version of the platform
Android app requires Google Play Services: No
Requires a phone number: No
Requires an email address: No
Your ID contains personal information: No
Data is locally encrypted: Yes
Encrypted by default: Yes
Perfect forward secrecy: Yes
Messages stored on server: Temporarily
Ephemeral messages: Yes
Puddle test: Data not recoverable Messages not saved on the server, only on each device. Contacts are recovered.
Hammer test: Data not recoverable Every message is ephemeral, chats can be manually deleted.
Has contact verification: Yes
Leaks files: No
Android app trackers (3): Bugsnag, Countly, Google Firebase Analytics
Websites: Secure Messaging Protocol source
Version tested: 4.62.0
Last tested: 10/30/2018
Notes:
June 2021- Amazon acquires Wickr to add to its AWS service offerings: https://www.slashgear.com/amazon-buys-wickr-a-secure-messaging-platform-even-the-nsa-likes-25679984/. This looks like a way to secure future contracts with the US Govt.
Partially open source (cypto protocol only)
1/24/2020- Received FIPs certification for crypto module
WickrMe synchronizes your chats across all your devices. Actually what happens is there is a separate message encrypted for each registered device you have. So if any devices are offline, those messages will be stored temporarily on the server until the device is online and is able to retrieve the message. Messages are stored for up to 6 days, after which they expire and are deleted from the server.
All messages expire, with the timeout beginning once the message has been read. You can choose a timeout of up to 6 days. This is a nice feature that you can have peace of mind that all messages will be deleted.
The desktop clients work very well and make it easy to transition between messaging on a mobile devices and doing so on a desktop. It is available for all major platforms including Ubuntu Linux.
There are not many unique features, but as a basic chat client it works very well. It has video chat (I haven't tried that yet), audio messages and file transfers. Notifications are reliable even on Lineage for MicroG.
Encryption process (from the wiki):
Each device that a WickrMe user uses is considered a node with it's own set of encryption keys. Each node creates a pool of asymmetric Diffie-Hellman public key pairs and sends the public keys to the WickrMe server. These are available for other nodes to use for sending messages.
When sending a message, a copy of the encrypted message packet is sent to all of the nodes of the recipient, plus to all the other nodes of the sender so that all the sender's devices also remain in sync. Every node receives an exact copy of the same message bundle, it is packaged so that all recipient nodes can decrypt the same message bundle.
One random symmetric key is generated which encrypts the actual message data. Then a new public key pair is generated on the sender's device to use once for this message bundle. One public key is retrieved from the pool of each node that will receive the message. The sender node's private key and each one of the repient nodes' public key is used to encrypt the symmetric message encryption key. So there will be N copies of the symmetric key encrypted and included in the message bundle. Then the encrypted message data, all the encrypted copies of the symmetric key and the public key of the sender's node is packaged together into the final message bundle which is sent to all the recipient nodes.
So one important question with this model, is it a risk having data (in this instance it happens to be the symmetric message encryption key) encrypted multiple times with different key pairs for each recipient and having all those copies included with the message bundle for all other recipents to access? If one node receives encrypted data intended for all the other nodes, encrypted with their keys, doesn't that expose a risk that one node could break the private key used by another node? The answer is yes that is a theoretical risk, but not a practical one. The reason is that each public key used to encrypt the actual message encryption key is only ever used once then destroyed. So yes having a known piece of data encrypted with multiple keys does make it theoretically easier to break any of the other secret keys needed to decrypt the message. However, this message was also sent to you, so you already know the contents of this message! Nothing is revealed that you do not already know. And since any private keys you may discover are never used again, they cannot be used to decrypt any other messages. (Note, I sent a question to Wickr and confirmed with them that in fact each public/private key pair between nodes is only used one time and discarded.)
My verdict: One of the very best, however concerns about country jurisdiction and trackers and ownership!
This app has a complete set of security features, and is practically "foolproof", by which I mean you can just use it and not worry about doing something that will compromise the security of your messages. At most your messages will sit around on your chat partners device or the WickrMe server (encrypted of course) for 6 days before being automatically deleted. Also it requires no personal information making it very anonymous. It does what it is supposed to do simply without a lot of flash.
The only downside is that the system is owned by Amazon and based in the USA (part of the 5 eyes) and I usually stay away from any messaging apps with servers there. However I am very confident in the security and anonymity of the system so this is one of the few messengers based in the US that I do use. You can also see their transparency report. The three trackers in the app are more than I would prefer it to have as well.
Platforms: Android (Direct APK), iOS, MacOS, Windows, Linux (Ubuntu, Debian, AppImage), Web
Communication types: Text, voice, video, file sharing
Country of origin: Switzerland
Source code: open
Encryption protocol: NaCl
Shared Secret exchange: ECDH25519
Message Encryption Cipher: ChaCha20
Business model: Enterprise version of the platform
Android app requires Google Play Services: Yes
Requires a phone number: Either
Requires an email address: Either
Your ID contains personal information: No
Data is locally encrypted: Yes
Encrypted by default: Yes
Perfect forward secrecy: Yes
Messages stored on server: Yes
Ephemeral messages: Yes
Puddle test: Data recoverable Messages are saved on the server
Hammer test: Data not recoverable Wire has an option to delete messages from all participant's devices.
Has contact verification: Yes
Leaks files: No
Android app trackers (1): Countly
Websites: Source code, Wire Audit, Security White Paper, Privacy White Paper
Version tested: 3.61.965
Last tested: 1/1/2021
Notes:
Update on 1/1/2021:
Wire has had some changes in ownership by getting some venture capital funding from U.S. sources. The focus of the app is switching to enterprise use but there is still the ability to use it on a personal level for free. The features in Wire are among the best available so hopefully the personal use of the app will not be completely removed.
Some information to reference:
PrivacyTools.io discussion started on Nov 4, 2019
Wire releases statement on blog on Nov 12, 2019
TechCrunch article with more info on Nov 13, 2019
Morpheus Capital Ventures portfolio claiming ownership of Wire
Review notes prior to 11/14/2019 are below for reference:
My verdict: Very solid app with great interface, I would consider this the best of a field of not so optimal choices when used on a desktop, using on multiple devices or needing video chat for more than one person.
This is one of the best apps as far as features and usability, and while not perfect gives you great security as well. With apps that sync across multiple devices it is also great at keeping a conversation going no matter what device you are using.
Wire is now focused on delivering enterprise services, has removed all references to personal use of Wire from its website but you can still register for personal use in the app. Other similar products are WickrMe (U.S.) and BBMe (Canada).
Communication types: Text, voice, video, file sharing
Country of origin: Switzerland
Source code: open
Encryption protocol: NaCl
Shared Secret exchange: ECDH25519
Message Encryption Cipher: ChaCha20
Business model: Enterprise version of the platform
Android app requires Google Play Services: Yes
Requires a phone number: Either
Requires an email address: Either
Your ID contains personal information: No
Data is locally encrypted: Yes
Encrypted by default: Yes
Perfect forward secrecy: Yes
Messages stored on server: Yes
Ephemeral messages: Yes
Puddle test: Data recoverable Messages are saved on the server
Hammer test: Data not recoverable Wire has an option to delete messages from all participant's devices.
Has contact verification: Yes
Leaks files: No
Android app trackers (1): Countly
Websites: Source code, Wire Audit, Security White Paper, Privacy White Paper
Version tested: 3.61.965
Last tested: 1/1/2021
Notes:
Update on 1/1/2021:
Wire has had some changes in ownership by getting some venture capital funding from U.S. sources. The focus of the app is switching to enterprise use but there is still the ability to use it on a personal level for free. The features in Wire are among the best available so hopefully the personal use of the app will not be completely removed.
Some information to reference:
PrivacyTools.io discussion started on Nov 4, 2019
Wire releases statement on blog on Nov 12, 2019
TechCrunch article with more info on Nov 13, 2019
Morpheus Capital Ventures portfolio claiming ownership of Wire
Review notes prior to 11/14/2019 are below for reference:
Server code open sourced
CrySP Wire analysis:
- Wire client sends the unencrypted, unhashed password to the central server over TLS, the server hashes the plaintext password with scrypt, and the hash is compared to the hash stored by the server. This process leaks the user's password to the central server; the server operators (or anyone who compromises the server) could log all of the plaintext passwords as users authenticate.
- The desktop application is implemented as a packaged web application
[Information provided by JR, updated by Perflyst on 1/28/2018]
What the server sees and may save:
- Your contact list is saved to the server hashed.
- Who you talk to, when, and for how long. (Needed for syncing multiple devices)[Information provided by SPC]
On some small number of Android devices notifications are an issue. The Wire support page lists a number of possible solutions that require user intervention that other messenger apps don't seem to have. The Android app issue tracker consistently has notification bugs for Android opened.
From the Privacy White Paper:
5 Usage data
Wire client applications can collect usage data with the aim of improving future
versions of Wire. Usage data helps Wire engineers to assess how Wire is used
and to identify areas of improvement. Usage data doesn’t contain personally
identifiable information.
Users can disable usage data collection at any time.
5.1 Types of usage data
Wire client applications collect several types of usage data:
• Crash reports
• Aggregated usage statistics
5.1.1 Crash reports
Crash reports are the version-specific per-event application state snapshots generated
in the event of an execution failure. Usually the crash reports are generated
when the application was terminated unexpectedly by the operating system.
Crash reports help Wire to understand what went wrong and to release bugfixes
faster.
5.1.2 Aggregated usage statistics
This type of data aggregates the various metrics of the application’s usage, such
as the amount of text messages sent, images posted and calls placed as well as
user interface flow data and events, such as a dropped call.
This statistical data helps Wire to improve future versions.
5.2 Usage and storage
Initially the data collected is stored on the users’ devices. It is synchronized
periodically with Wire and third-party services. Crash and exception reports
are stored on HockeyApp [1] and Raygun [2]. All other types of usage data are
stored on the Localytics [3] and Mixpanel [4] services.
So be sure to turn off the analytics settings under Settings and Advanced:
When you install Wire on a new device you are notified by email, which is a great way to know about unauthorized installs.
Massive battery usage on some older Android versions and forks like CopperheadOS without Google Play Services:
Stock Android 8.1 battery usage is much more in line with other messenger apps.
Encryption process (from the whitepaper):
Wire uses Proteus, "an independent implementation of the Axolotl/Double Ratchet protocol"
Every client (a chat participant may have multiple clients, or devices) generates a set of pre-keys for others to use for encryption to the client. The pre-keys are uploaded to the Wire server. To create a new key pair with a chat participant's client one of their pre-keys is downloaded from the server. That pre-key is then removed from the server so that each pre-key is used only once. The sender generates their own pre-key, then the combination of the two pre-keys are used to generate the encryption key for that client. The message is encrypted using that key, and if this is the first transaction with the client the sender's pre-key is bundled with the message so that the recipient's client can generate the decryption key. When sending the message to multiple clients the message is encrypted once for each client, and the bundle is sent to the Wire server for delivery to each one.
Once an initial message is sent to establish the key used between two clients, ratcheting is used to automatically advance to new keys during multiple message exchanges. This provides forward secrecy for the encrypted message and also allows messages to be ephemeral.
My verdict: Very solid app with great interface, I would consider this the best of a field of not so optimal choices when used on a desktop, using on multiple devices or needing video chat for more than one person.
This is one of the best apps as far as features and usability, and while not perfect gives you great security as well. With apps that sync across multiple devices it is also great at keeping a conversation going no matter what device you are using.
Wire is now focused on delivering enterprise services, has removed all references to personal use of Wire from its website but you can still register for personal use in the app. Other similar products are WickrMe (U.S.) and BBMe (Canada).
Platforms: Android, iOS, MacOS, Windows
Communication types: Text, group messaging, voice and video messages, file sharing
Country of origin: USA
Source code: closed
Encryption protocol: ?
Shared Secret exchange: ?
Message Encryption Cipher: ?
Business model: Subscription plans for premium features or enterprise
Android app requires Google Play Services: Yes
Requires a phone number: Either
Requires an email address: Either
Your ID contains personal information: Email
Data is locally encrypted: N/A (messages deleted immediately)
Encrypted by default: Yes
Perfect forward secrecy: No
Messages stored on server: Temporarily
Ephemeral messages: Yes
Puddle test: Data not recoverable Messages are deleted as soon as they are read.
Hammer test: Data not recoverable Messages are deleted as soon as they are read.
Has contact verification: No
Leaks files: No
Android app trackers (4): Facebook Login, Facebook Share, Google CrashLytics, Google Firebase Analytics
Websites: FAQ, Security Audit
Version tested: 5.3.5
Last tested: 1/25/2018
Notes:
Messages are destroyed after they are read
My verdict: Stay Away!
It is very concerning that such lax security practices (weak password rules, no message authentication or integrity validation) were allowed to be a part of the design in the first place.
Also the desktop clients are written in JavaScript which is easily modified to bypass security checks.
Did they fix these issues? Maybe but without open code to inspect we cannot know.
Communication types: Text, group messaging, voice and video messages, file sharing
Country of origin: USA
Source code: closed
Encryption protocol: ?
Shared Secret exchange: ?
Message Encryption Cipher: ?
Business model: Subscription plans for premium features or enterprise
Android app requires Google Play Services: Yes
Requires a phone number: Either
Requires an email address: Either
Your ID contains personal information: Email
Data is locally encrypted: N/A (messages deleted immediately)
Encrypted by default: Yes
Perfect forward secrecy: No
Messages stored on server: Temporarily
Ephemeral messages: Yes
Puddle test: Data not recoverable Messages are deleted as soon as they are read.
Hammer test: Data not recoverable Messages are deleted as soon as they are read.
Has contact verification: No
Leaks files: No
Android app trackers (4): Facebook Login, Facebook Share, Google CrashLytics, Google Firebase Analytics
Websites: FAQ, Security Audit
Version tested: 5.3.5
Last tested: 1/25/2018
Notes:
Messages are destroyed after they are read
[Information provided by "C"]
That Encrypted Chat App the White House Liked? Full of Holes
Which links to: Make Confide great again? No, we cannot
My verdict: Stay Away!
It is very concerning that such lax security practices (weak password rules, no message authentication or integrity validation) were allowed to be a part of the design in the first place.
Also the desktop clients are written in JavaScript which is easily modified to bypass security checks.
Did they fix these issues? Maybe but without open code to inspect we cannot know.
Platforms: Android, iOS, Mac, Windows, Web
Communication types: Text, group chat, photos, files, location
Country of origin: Norway
Source code: partialopen
Encryption protocol: ?
Shared Secret exchange: El-Gamal EC384
Message Encryption Cipher: AES-256
Business model: Enterprise version of the platform
Android app requires Google Play Services: Yes
Requires a phone number: Yes
Requires an email address: Yes
Your ID contains personal information: Email
Data is locally encrypted: Yes
Encrypted by default: Yes
Perfect forward secrecy: Yes
Messages stored on server: Yes
Ephemeral messages: No
Puddle test: Data recoverable Messages are saved on the server.
Hammer test: Data recoverable Android client leaks files
Has contact verification: Yes
Leaks files: Android
Android app trackers (1): Google Firebase Analytics
Websites: Source code, Whitepaper
Version tested: 3.4.2
Last tested: 3/14/2019
Notes:
Crypho is a multi-device secure communications platform based in Norway. They offer enterprise level subscriptions but also a free personal level option.
When signing up for an account you must first give an email address and verify it is yours by clicking on a link they will send you. This email will become part of your profile so it cannot be a temporary or throw away address. Once your email is verified, then you must give them your phone number to use for their 2 factor authentication. Their website claims you can use an authenticator application but I never saw a way to make that choice. You will be sent an SMS message when logging in as a 2 factor authentication.
To add a contact of another Crypho user you must enter their email address to send them an invite. This is why you need to use a real email address, an invite will come through email to be able to complete the contact connection process.
When sending an image from my Android device a copy of it showed up in /Android/com.crypho.app/files/Pictures. I did not see any copies of photos received in chats on the Android however. When opening photos in the chat session it did take a second for them to open up, indicating to me that they were being decrypted on the fly from an encrypted storage location. So having a copy of a photo sent stored in public storage seems like an unfortunate slip-up.
The use of El-Gamal keys is questionable. This algorithm is vulnerable to message malliability- which means that the encrypted cyphertext can be altered and it will change the plain text that is decrypted. Without message integrity checks this manipulation could be missed. In this case what is encrypted is the actual message encryption key, so if the encrypted key's cipher text is altered, the decrypted key would also be altered but it would be unable to decrypt the actual message ciphertext. So there isn't really a risk of the message being exposed, it will just become undecipherable.
My verdict: Too much personal info required
The fact you must give both a valid email and phone number is too much I think. And for others to contact you they must know your email. There are other apps that are better and expose less personal information.
Communication types: Text, group chat, photos, files, location
Country of origin: Norway
Source code: partialopen
Encryption protocol: ?
Shared Secret exchange: El-Gamal EC384
Message Encryption Cipher: AES-256
Business model: Enterprise version of the platform
Android app requires Google Play Services: Yes
Requires a phone number: Yes
Requires an email address: Yes
Your ID contains personal information: Email
Data is locally encrypted: Yes
Encrypted by default: Yes
Perfect forward secrecy: Yes
Messages stored on server: Yes
Ephemeral messages: No
Puddle test: Data recoverable Messages are saved on the server.
Hammer test: Data recoverable Android client leaks files
Has contact verification: Yes
Leaks files: Android
Android app trackers (1): Google Firebase Analytics
Websites: Source code, Whitepaper
Version tested: 3.4.2
Last tested: 3/14/2019
Notes:
Crypho is a multi-device secure communications platform based in Norway. They offer enterprise level subscriptions but also a free personal level option.
When signing up for an account you must first give an email address and verify it is yours by clicking on a link they will send you. This email will become part of your profile so it cannot be a temporary or throw away address. Once your email is verified, then you must give them your phone number to use for their 2 factor authentication. Their website claims you can use an authenticator application but I never saw a way to make that choice. You will be sent an SMS message when logging in as a 2 factor authentication.
To add a contact of another Crypho user you must enter their email address to send them an invite. This is why you need to use a real email address, an invite will come through email to be able to complete the contact connection process.
When sending an image from my Android device a copy of it showed up in /Android/com.crypho.app/files/Pictures. I did not see any copies of photos received in chats on the Android however. When opening photos in the chat session it did take a second for them to open up, indicating to me that they were being decrypted on the fly from an encrypted storage location. So having a copy of a photo sent stored in public storage seems like an unfortunate slip-up.
The use of El-Gamal keys is questionable. This algorithm is vulnerable to message malliability- which means that the encrypted cyphertext can be altered and it will change the plain text that is decrypted. Without message integrity checks this manipulation could be missed. In this case what is encrypted is the actual message encryption key, so if the encrypted key's cipher text is altered, the decrypted key would also be altered but it would be unable to decrypt the actual message ciphertext. So there isn't really a risk of the message being exposed, it will just become undecipherable.
My verdict: Too much personal info required
The fact you must give both a valid email and phone number is too much I think. And for others to contact you they must know your email. There are other apps that are better and expose less personal information.
Platforms: Android, iOS
Communication types: Chat, files, videos, location, voice calls
Country of origin: Germany
Source code: closed
Encryption protocol: CSMP
Shared Secret exchange: CVBlockchain
Message Encryption Cipher: Salsa20
Business model: CV Secure Business and CVCore SaaS enterprise subscriptions
Android app requires Google Play Services: N/A
Requires a phone number: No
Requires an email address: No
Your ID contains personal information: No
Data is locally encrypted: Yes
Encrypted by default: Yes
Perfect forward secrecy: ?
Messages stored on server: ?
Ephemeral messages: Yes
Puddle test: Data recoverable Features multi-device synchronization
Hammer test: Data not recoverable Able to destroy messages on both ends of chat.
Has contact verification: No
Leaks files: No
Android app trackers (4): AppsFlyer, Flurry, Google CrashLytics, Google Firebase Analytics
Websites: Whitepaper, Medium- The Nitty Gritty of It All. Crypviser Unleased.
Version tested: Android- 1.2.3, iOS- 1.9.5
Last tested: 12/22/2018
Notes:
Crypviser is unique messaging application that uses a public blockchain to store half of the public key of all users. This is claimed to prevent man in the middle attacks because the integrity of the public key can be verified against the blockchain.
Each chat can be password protected or hidden with a password. Individual messages or the entire chat can be deleted on both sides. The application interface is nicely done and is easy to navigate. The are Crypvisor tokens (CVT) that you can send to others within the applications.
During testing there was a message that appeared to be sent, but it was never received. Several times the application crashed (Android version). Sometimes messages that were set to expire had the timer stop, and so were ever deleted after the timeout period. I was not able to successfully set a profile folder, after choosing a photo to use the avatar just never changed from the generic person graphic.
The use of blockchain is a good effort to try to ensure integrity of a public key. The first half of the key is stored iin publicly accessible blockchain, the other half is stored on the CV servers. This forces the clients to use the CV server for ID validation and acquiring half of the public key needed to encrypt messages. While the ID verification using the CV server is nice, it would still be good to have contact verification via some key fingerprint as a manual verification.
From the whitepaper:
My verdict: Interesting, too many bugs
There were several bugs, but overall the app has a nice look. Message delivery was not 100% reliable and the Android app crashed several times. Some expiring messages failed to delete after the set timeout period.
The use of blockchain is unique, however only half of the public key is stored in blockchain. This means you are still dependent on and must trust the CV server to provide user identification verification and the second half of the public key. This may be changing with the 2.0 version of the blockchain (see the whitepaper).
Communication types: Chat, files, videos, location, voice calls
Country of origin: Germany
Source code: closed
Encryption protocol: CSMP
Shared Secret exchange: CVBlockchain
Message Encryption Cipher: Salsa20
Business model: CV Secure Business and CVCore SaaS enterprise subscriptions
Android app requires Google Play Services: N/A
Requires a phone number: No
Requires an email address: No
Your ID contains personal information: No
Data is locally encrypted: Yes
Encrypted by default: Yes
Perfect forward secrecy: ?
Messages stored on server: ?
Ephemeral messages: Yes
Puddle test: Data recoverable Features multi-device synchronization
Hammer test: Data not recoverable Able to destroy messages on both ends of chat.
Has contact verification: No
Leaks files: No
Android app trackers (4): AppsFlyer, Flurry, Google CrashLytics, Google Firebase Analytics
Websites: Whitepaper, Medium- The Nitty Gritty of It All. Crypviser Unleased.
Version tested: Android- 1.2.3, iOS- 1.9.5
Last tested: 12/22/2018
Notes:
Note: I recommend avoiding Crypviser at all costs! Their CTO Vadim Andryan is acting very unprofessionally and spreading FUD about other secure messengers being under the control of the Russian government. I will not link to the article here, but you can find it at medium[dot]com under his username "@vadiman". The Russian government passed a draconian law "requiring" messaging apps to give them access to all data, and using this fact to assume that messengers are now under Russian control and writing an article claiming this as fact is sleazy. Crypviser is not interested in the secure messaging community, they are just trying to make money with their app that uses their blockchain.
Crypviser is unique messaging application that uses a public blockchain to store half of the public key of all users. This is claimed to prevent man in the middle attacks because the integrity of the public key can be verified against the blockchain.
Each chat can be password protected or hidden with a password. Individual messages or the entire chat can be deleted on both sides. The application interface is nicely done and is easy to navigate. The are Crypvisor tokens (CVT) that you can send to others within the applications.
During testing there was a message that appeared to be sent, but it was never received. Several times the application crashed (Android version). Sometimes messages that were set to expire had the timer stop, and so were ever deleted after the timeout period. I was not able to successfully set a profile folder, after choosing a photo to use the avatar just never changed from the generic person graphic.
The use of blockchain is a good effort to try to ensure integrity of a public key. The first half of the key is stored iin publicly accessible blockchain, the other half is stored on the CV servers. This forces the clients to use the CV server for ID validation and acquiring half of the public key needed to encrypt messages. While the ID verification using the CV server is nice, it would still be good to have contact verification via some key fingerprint as a manual verification.
From the whitepaper:
The next generation of Crypviser 2.0 will be based on the new kind of Blockchain especially designed for the reliable encryption keys exchange and authentication purposes in instant communication networks. Crypviser Blockchain will be represented as a first mobile Blockchain, where every device will operate as a node to serve transactions of encryption keys exchange and validation.
My verdict: Interesting, too many bugs
There were several bugs, but overall the app has a nice look. Message delivery was not 100% reliable and the Android app crashed several times. Some expiring messages failed to delete after the set timeout period.
The use of blockchain is unique, however only half of the public key is stored in blockchain. This means you are still dependent on and must trust the CV server to provide user identification verification and the second half of the public key. This may be changing with the 2.0 version of the blockchain (see the whitepaper).
Platforms: Android, iOS, Web
Communication types: Chat, group chat, cloud file storage, video chat, screen sharing, voice, calendar, notes
Country of origin: UK
Source code: closed
Encryption protocol: FortKnoxster
Shared Secret exchange: ECDH P521
Message Encryption Cipher: AES-256
Business model: Purchasing additional cloud storage, future enterprise platform
Android app requires Google Play Services: No
Requires a phone number: Yes
Requires an email address: No
Your ID contains personal information: No
Data is locally encrypted: ?
Encrypted by default: Yes
Perfect forward secrecy: For mail yes, others ?
Messages stored on server: Yes
Ephemeral messages: No
Puddle test: Data recoverable Messages are stored on the server.
Hammer test: Data recoverable Android app leaks files.
Has contact verification: No
Leaks files: Android
Android app trackers (3): AppsFlyer, Google CrashLytics, Google Firebase Analytics
Websites: Whitepaper
Version tested: 1.0.9
Last tested: 7/16/2018
Notes:
Signing up can be a bit tricky because only certain web browsers on a PC are allowed to be used: Chrome, Firefox or Opera. You can also sign up through the mobile app.
This product is more of a suite of systems, chat, email, cloud file storage, etc. You can earn credits in the FKX cryptocurrency for hosting distributed cloud files, which can then be used to purchase FortKnoxster services. No prices are available at this time.
On the mobile apps finding contacts is by their phone number, which is why the app asks for access to your contact list. You canot just enter a phone number manually to invite someone. It will then send them an SMS message. Strangely, inviting a contact on the web version asks you to enter their email address without requesting access to an address book.
The web application has more features like file storage, it is not functional yet.
I did find one unencrypted image on the device data storage, which is of concern.
Transferring to another device is easy, simply install the app and log in. All contacts and chat history are loaded onto the new device. This is good if you want this feature, however this does mean all this data is saved on their servers.
My verdict:
This app has potential, however I do not like that a phone number is required to register and search for other contacts. They are based in the Gibraltar which falls under UK law. At this time I would say pass, but keep an eye on this.
Communication types: Chat, group chat, cloud file storage, video chat, screen sharing, voice, calendar, notes
Country of origin: UK
Source code: closed
Encryption protocol: FortKnoxster
Shared Secret exchange: ECDH P521
Message Encryption Cipher: AES-256
Business model: Purchasing additional cloud storage, future enterprise platform
Android app requires Google Play Services: No
Requires a phone number: Yes
Requires an email address: No
Your ID contains personal information: No
Data is locally encrypted: ?
Encrypted by default: Yes
Perfect forward secrecy: For mail yes, others ?
Messages stored on server: Yes
Ephemeral messages: No
Puddle test: Data recoverable Messages are stored on the server.
Hammer test: Data recoverable Android app leaks files.
Has contact verification: No
Leaks files: Android
Android app trackers (3): AppsFlyer, Google CrashLytics, Google Firebase Analytics
Websites: Whitepaper
Version tested: 1.0.9
Last tested: 7/16/2018
Notes:
Update- 7/16/2018
FortKnoxster is now out of beta. Some changes are that you now need to provide a phone number instead of en email address when signing up (bad). Your profile ID is no longer your email address and can be anything you choose (good). To add contacts you need to grant the application access to your phone's contacts list (bad).
Signing up can be a bit tricky because only certain web browsers on a PC are allowed to be used: Chrome, Firefox or Opera. You can also sign up through the mobile app.
This product is more of a suite of systems, chat, email, cloud file storage, etc. You can earn credits in the FKX cryptocurrency for hosting distributed cloud files, which can then be used to purchase FortKnoxster services. No prices are available at this time.
On the mobile apps finding contacts is by their phone number, which is why the app asks for access to your contact list. You canot just enter a phone number manually to invite someone. It will then send them an SMS message. Strangely, inviting a contact on the web version asks you to enter their email address without requesting access to an address book.
The web application has more features like file storage, it is not functional yet.
I did find one unencrypted image on the device data storage, which is of concern.
Transferring to another device is easy, simply install the app and log in. All contacts and chat history are loaded onto the new device. This is good if you want this feature, however this does mean all this data is saved on their servers.
My verdict:
This app has potential, however I do not like that a phone number is required to register and search for other contacts. They are based in the Gibraltar which falls under UK law. At this time I would say pass, but keep an eye on this.
Platforms: Android, iOS, Windows
Communication types: Text, photos, audio, files, appointments
Country of origin: UK
Source code: closed
Encryption protocol: ?
Shared Secret exchange: ?
Message Encryption Cipher: AES-256
Business model: Enterprise version of the platform
Android app requires Google Play Services: Yes
Requires a phone number: No
Requires an email address: No
Your ID contains personal information: No
Data is locally encrypted: Yes/No
Encrypted by default: No
Perfect forward secrecy: ?
Messages stored on server: ?
Ephemeral messages: Yes
Puddle test: ?
Hammer test: Data recoverable Android leaks files
Has contact verification: No
Leaks files: Android
Android app trackers (4): Facebook Analytics, Facebook Login, Facebook Places, Facebook Share
Websites:
Version tested: 0.9.177
Last tested: 3/16/2019
Notes:
This app is more focused on encrypted file sharing but it does have a secure messaging section. The features of the messaging were fairly standard. It does have a "Timed Delete" feature that is supposed to delete the message after the given time has expired but in testing we did have one message that did not delete.
To search for other get2clouds users you must grant access to the phone's contact list. Searching will not work without that access.
Despite there being some articles on their blog regarding Facebook data and profile gathering, this app has 4 Facebook trackers in it. Hmm.
While I did find user avatars stored in public file storage on Android at /get2clouds I did not find any other files or photos that were sent in messages.
My verdict: No thanks, Facebook tracking.
I am concerned about the access required for your phone's contacts list, but then add the Faceook trackers to it and this is a definate no!
Communication types: Text, photos, audio, files, appointments
Country of origin: UK
Source code: closed
Encryption protocol: ?
Shared Secret exchange: ?
Message Encryption Cipher: AES-256
Business model: Enterprise version of the platform
Android app requires Google Play Services: Yes
Requires a phone number: No
Requires an email address: No
Your ID contains personal information: No
Data is locally encrypted: Yes/No
Encrypted by default: No
Perfect forward secrecy: ?
Messages stored on server: ?
Ephemeral messages: Yes
Puddle test: ?
Hammer test: Data recoverable Android leaks files
Has contact verification: No
Leaks files: Android
Android app trackers (4): Facebook Analytics, Facebook Login, Facebook Places, Facebook Share
Websites:
Version tested: 0.9.177
Last tested: 3/16/2019
Notes:
This app is more focused on encrypted file sharing but it does have a secure messaging section. The features of the messaging were fairly standard. It does have a "Timed Delete" feature that is supposed to delete the message after the given time has expired but in testing we did have one message that did not delete.
To search for other get2clouds users you must grant access to the phone's contact list. Searching will not work without that access.
Despite there being some articles on their blog regarding Facebook data and profile gathering, this app has 4 Facebook trackers in it. Hmm.
While I did find user avatars stored in public file storage on Android at /get2clouds I did not find any other files or photos that were sent in messages.
My verdict: No thanks, Facebook tracking.
I am concerned about the access required for your phone's contacts list, but then add the Faceook trackers to it and this is a definate no!
Platforms: Android, iOS
Communication types: Text, group chat, images, videos, location, contacts, files
Country of origin: Germany
Source code: closed
Encryption protocol: ?
Shared Secret exchange: ?
Message Encryption Cipher: ?
Business model: Enterprise version of the platform
Android app requires Google Play Services: Yes
Requires a phone number: Yes
Requires an email address: No
Your ID contains personal information: Phone
Data is locally encrypted: Yes
Encrypted by default: Yes
Perfect forward secrecy: No
Messages stored on server: Temporarily
Ephemeral messages: Yes
Puddle test: Data not recoverable Messages saved only on device.
Hammer test: Data not recoverable When messages are deleted on all devices.
Has contact verification: Yes
Leaks files: No
Android app trackers (0): None
Websites:
Version tested: 3.0.0.292474 (Android), 3.0 (iOS)
Last tested: 6/30/2019
Notes:
Note: Ginlo will be shutting down at the end of 2019.
Ginlo was originally Developed by the Deutsche Post under the name SIMSme, then the app was transferred to Brabbler to maintain and was renamed Ginlo.
The Ginlo encryption key is tied to the phone and cannot be transfered to another. Requires a phone number to register.
Invite contacts based on their phone number, email address or Ginlo ID.
Self destructing messages can be set to auto delete from 1 to 60 seconds after being read or at a specific date and time that you choose. There does not seem to be any restriction on choosing the date manually (except of course it must be in the future). When receiving a self destruct message you must touch on the message and then touch and hold on the screen to view it.
My verdict: Solid app to communicate with those who know your phone number
This app is well done, didn't find any major issues with the app or functionality. It offers great features like self destruct messages and delayed sending. This does require that your contacts know your phone number which is the only real drawback of this app.
Communication types: Text, group chat, images, videos, location, contacts, files
Country of origin: Germany
Source code: closed
Encryption protocol: ?
Shared Secret exchange: ?
Message Encryption Cipher: ?
Business model: Enterprise version of the platform
Android app requires Google Play Services: Yes
Requires a phone number: Yes
Requires an email address: No
Your ID contains personal information: Phone
Data is locally encrypted: Yes
Encrypted by default: Yes
Perfect forward secrecy: No
Messages stored on server: Temporarily
Ephemeral messages: Yes
Puddle test: Data not recoverable Messages saved only on device.
Hammer test: Data not recoverable When messages are deleted on all devices.
Has contact verification: Yes
Leaks files: No
Android app trackers (0): None
Websites:
Version tested: 3.0.0.292474 (Android), 3.0 (iOS)
Last tested: 6/30/2019
Notes:
Note: Ginlo will be shutting down at the end of 2019.
Ginlo was originally Developed by the Deutsche Post under the name SIMSme, then the app was transferred to Brabbler to maintain and was renamed Ginlo.
The Ginlo encryption key is tied to the phone and cannot be transfered to another. Requires a phone number to register.
Invite contacts based on their phone number, email address or Ginlo ID.
Self destructing messages can be set to auto delete from 1 to 60 seconds after being read or at a specific date and time that you choose. There does not seem to be any restriction on choosing the date manually (except of course it must be in the future). When receiving a self destruct message you must touch on the message and then touch and hold on the screen to view it.
My verdict: Solid app to communicate with those who know your phone number
This app is well done, didn't find any major issues with the app or functionality. It offers great features like self destruct messages and delayed sending. This does require that your contacts know your phone number which is the only real drawback of this app.
Platforms: Android, iOS
Communication types: Text, photos, files, video, stickers
Country of origin: Canada
Source code: closed
Encryption protocol: ?
Shared Secret exchange: ?
Message Encryption Cipher: AES-256
Business model: ?
Android app requires Google Play Services: No
Requires a phone number: Yes
Requires an email address: No
Your ID contains personal information: No
Data is locally encrypted: Yes
Encrypted by default: No
Perfect forward secrecy: Yes
Messages stored on server: Yes
Ephemeral messages: Yes
Puddle test: Data recoverable Messages in the encrypted vault are saved to the cloud.
Hammer test: Data recoverable Android app leaks files.
Has contact verification: No
Leaks files: Android
Android app trackers (2): Google CrashLytics, Google Firebase Analytics
Websites: FAQ
Version tested: 2.6.1311
Last tested: 4/10/2018
Notes:
Alias accounts can be created and linked to your master account.
There is a "Vault" where you can store files encrypted by a password.
The app asks for permission to access your contacts. If you deny this, it will ask again every time you open the app which is annoying.
Remotely delete all HoopMessenger data on a lost device.
Currently only chats in the vault are end to end encrypted. They do plan to make all chats E2EE in the future.
Android leaks files: found photos in Local Storage/Device Storage/Android/data/com.magnificus.hoop/files.
My Verdict:
This messenger has a lot of promise and some great features. I really like the alias option where you can hide your phone number. Unfortunately not all chats are end to end encrypted, only those within the vault. That is a security risk but they do mention that they are working on making all chats E2EE.
Whenever you get out of the application and then go back in, you must re-enter the vault password to get to your encrypted messages. This is good security, but makes using the secure messaging part more cumbersome. This is a great app to try, but I think it would be better to wait until all messages are E2EE before using this extensively. Also the leakage of files needs to be fixed.
Communication types: Text, photos, files, video, stickers
Country of origin: Canada
Source code: closed
Encryption protocol: ?
Shared Secret exchange: ?
Message Encryption Cipher: AES-256
Business model: ?
Android app requires Google Play Services: No
Requires a phone number: Yes
Requires an email address: No
Your ID contains personal information: No
Data is locally encrypted: Yes
Encrypted by default: No
Perfect forward secrecy: Yes
Messages stored on server: Yes
Ephemeral messages: Yes
Puddle test: Data recoverable Messages in the encrypted vault are saved to the cloud.
Hammer test: Data recoverable Android app leaks files.
Has contact verification: No
Leaks files: Android
Android app trackers (2): Google CrashLytics, Google Firebase Analytics
Websites: FAQ
Version tested: 2.6.1311
Last tested: 4/10/2018
Notes:
Alias accounts can be created and linked to your master account.
There is a "Vault" where you can store files encrypted by a password.
The app asks for permission to access your contacts. If you deny this, it will ask again every time you open the app which is annoying.
Remotely delete all HoopMessenger data on a lost device.
Currently only chats in the vault are end to end encrypted. They do plan to make all chats E2EE in the future.
Android leaks files: found photos in Local Storage/Device Storage/Android/data/com.magnificus.hoop/files.
My Verdict:
This messenger has a lot of promise and some great features. I really like the alias option where you can hide your phone number. Unfortunately not all chats are end to end encrypted, only those within the vault. That is a security risk but they do mention that they are working on making all chats E2EE.
Whenever you get out of the application and then go back in, you must re-enter the vault password to get to your encrypted messages. This is good security, but makes using the secure messaging part more cumbersome. This is a great app to try, but I think it would be better to wait until all messages are E2EE before using this extensively. Also the leakage of files needs to be fixed.
Platforms: Android, iOS
Communication types: Text, group chat, photos, files, voice, video, audio chat, video chat
Country of origin: Germany
Source code: closed
Encryption protocol: ?
Shared Secret exchange: ?
Message Encryption Cipher: ?
Business model: ?
Android app requires Google Play Services: Yes
Requires a phone number: No
Requires an email address: No
Your ID contains personal information: No
Data is locally encrypted: Yes
Encrypted by default: Yes
Perfect forward secrecy: ?
Messages stored on server: ?
Ephemeral messages: No
Puddle test: ?
Hammer test: ?
Has contact verification: Yes
Leaks files: No
Android app trackers (2): Matomo (Piwik), Googl Firebase Analytics
Websites:
Version tested: Android 1.8.2, iOS 2.13
Last tested: 1/1/2021
Notes:
Update 1/1/2021: There have been no updates to the application or social media posts for over a year so this looks like an abandoned project.
Kedr provides a good selection of messaging features including sharing audio clips and video chats. It also allows you to request the deletion of messages from all devices. I found no real issues or bugs with the app which worked very well.
I was not able to find very much information about the technical details of how the app works. The website has very little information, and the only thing I was able to find was when the app asks for permissions to access your contacts it gives the reason "to find other Matrix users based on their email and phone numbers". So I take this to mean that Kedr is using the Matrix protocol, however I am not able to confirm that yet. I did try to do a search for contacts using known Matrix accounts used on the main Matrix.org network, however no results were found so if this is based on Matrix it appears to be on a totally separate Matrix network. This might be a good thing if you are concerned about data privacy issues using Riot/Matrix.
Providing an email or phone number is optional, as well as giving access to your contacts list. I was also pleased that on Android I could not find any trace of files saved by Kedr in the public storage area so this app seems to have been built correctly regarding the safe storage of data in private app file space.
My verdict- I want to know more
Without technical details on how this app works I cannot give it a complete review, however I do like what I see. I found no major issues with usage or data privacy.
Communication types: Text, group chat, photos, files, voice, video, audio chat, video chat
Country of origin: Germany
Source code: closed
Encryption protocol: ?
Shared Secret exchange: ?
Message Encryption Cipher: ?
Business model: ?
Android app requires Google Play Services: Yes
Requires a phone number: No
Requires an email address: No
Your ID contains personal information: No
Data is locally encrypted: Yes
Encrypted by default: Yes
Perfect forward secrecy: ?
Messages stored on server: ?
Ephemeral messages: No
Puddle test: ?
Hammer test: ?
Has contact verification: Yes
Leaks files: No
Android app trackers (2): Matomo (Piwik), Googl Firebase Analytics
Websites:
Version tested: Android 1.8.2, iOS 2.13
Last tested: 1/1/2021
Notes:
Update 1/1/2021: There have been no updates to the application or social media posts for over a year so this looks like an abandoned project.
Kedr provides a good selection of messaging features including sharing audio clips and video chats. It also allows you to request the deletion of messages from all devices. I found no real issues or bugs with the app which worked very well.
I was not able to find very much information about the technical details of how the app works. The website has very little information, and the only thing I was able to find was when the app asks for permissions to access your contacts it gives the reason "to find other Matrix users based on their email and phone numbers". So I take this to mean that Kedr is using the Matrix protocol, however I am not able to confirm that yet. I did try to do a search for contacts using known Matrix accounts used on the main Matrix.org network, however no results were found so if this is based on Matrix it appears to be on a totally separate Matrix network. This might be a good thing if you are concerned about data privacy issues using Riot/Matrix.
Providing an email or phone number is optional, as well as giving access to your contacts list. I was also pleased that on Android I could not find any trace of files saved by Kedr in the public storage area so this app seems to have been built correctly regarding the safe storage of data in private app file space.
My verdict- I want to know more
Without technical details on how this app works I cannot give it a complete review, however I do like what I see. I found no major issues with usage or data privacy.
Platforms: Android, iOS, MacOS, Windows, Linux (many)
Communication types: Text, group chat, file sharing
Country of origin: USA
Source code: partialopen
Encryption protocol: NaCl
Shared Secret exchange: ECDH25519
Message Encryption Cipher: XSalsa20
Business model: Investors?
Android app requires Google Play Services: No
Requires a phone number: No
Requires an email address: Yes
Your ID contains personal information: No
Data is locally encrypted: Yes
Encrypted by default: Yes
Perfect forward secrecy: Only for "exploding" messages
Messages stored on server:
Ephemeral messages: Yes
Puddle test: Data recoverable
Hammer test: Data not recoverable When messages are deleted on all devices.
Has contact verification: No
Leaks files: No
Android app trackers (1): Google Firebase Analytics
Websites: Source code
Version tested: 5.5.0
Last tested: 12/31/2020
Notes:
Update in 2020: Keybase was sold to Zoom. The purchase was a talent acquisition, so it was the people and skills that Zoom wanted to get from the Keybase team to help Zoom imrove their encryption and security of the platform. Whether Keybase will continue is not known, but there is little chance for there to be very much work done on it for improvements or bug fixes going forward. So this is an unfortunate turn for this app and with the unknown future of the platform I would not recommend investing very much time into it if you are not already signed up.
You can also verify other website identities, GPG keys, domains, etc that you own.
Keybase adds "exploding" messages (ephemeral). Note these messages do use perfect forward secrecy, however regular non-ephemeral messages do not.
My verdict: Great for chat and other uses, but uncertain future
Keybase has several unique features, which now also includes secured personal and group file storage and sharing and encrypted git. It is also very easy for someone new to PGP to create a new key for themselves.
Note as of 12/31/2020 there have not been any updates to this application since it was sold to Zoom, so the future of this app looks dim.
Communication types: Text, group chat, file sharing
Country of origin: USA
Source code: partialopen
Encryption protocol: NaCl
Shared Secret exchange: ECDH25519
Message Encryption Cipher: XSalsa20
Business model: Investors?
Android app requires Google Play Services: No
Requires a phone number: No
Requires an email address: Yes
Your ID contains personal information: No
Data is locally encrypted: Yes
Encrypted by default: Yes
Perfect forward secrecy: Only for "exploding" messages
Messages stored on server:
Ephemeral messages: Yes
Puddle test: Data recoverable
Hammer test: Data not recoverable When messages are deleted on all devices.
Has contact verification: No
Leaks files: No
Android app trackers (1): Google Firebase Analytics
Websites: Source code
Version tested: 5.5.0
Last tested: 12/31/2020
Notes:
Update in 2020: Keybase was sold to Zoom. The purchase was a talent acquisition, so it was the people and skills that Zoom wanted to get from the Keybase team to help Zoom imrove their encryption and security of the platform. Whether Keybase will continue is not known, but there is little chance for there to be very much work done on it for improvements or bug fixes going forward. So this is an unfortunate turn for this app and with the unknown future of the platform I would not recommend investing very much time into it if you are not already signed up.
You can also verify other website identities, GPG keys, domains, etc that you own.
Keybase adds "exploding" messages (ephemeral). Note these messages do use perfect forward secrecy, however regular non-ephemeral messages do not.
My verdict: Great for chat and other uses, but uncertain future
Keybase has several unique features, which now also includes secured personal and group file storage and sharing and encrypted git. It is also very easy for someone new to PGP to create a new key for themselves.
Note as of 12/31/2020 there have not been any updates to this application since it was sold to Zoom, so the future of this app looks dim.
Platforms: Android (on F-Droid), Java client
Communication types: Text, photo, video, audio, files, location, contacts
Country of origin: None
Source code: open
Encryption protocol: OpenPGP
Shared Secret exchange: ECDH P256
Message Encryption Cipher: AES-192
Business model: Free open source project, servers run by volunteers
Android app requires Google Play Services: No
Requires a phone number: Yes
Requires an email address: No
Your ID contains personal information: Phone
Data is locally encrypted: No
Encrypted by default: Yes
Perfect forward secrecy: Yes
Messages stored on server: Yes
Ephemeral messages: No
Puddle test: ?
Hammer test: Data recoverable Android client leaks files
Has contact verification: Yes
Leaks files: Android
Android app trackers (2): Google CrashLytics, Google Firebase Analytics
Websites: Java Client source, Android client source
Version tested: 4.1.5
Last tested: 6/22/2018
Notes:
Pros:
On F-Droid
Not dependent on Google play services
Cons:
People have to know your phone#
Android only
Android leaks files: found photos in Local Storage/Device Storage/Pictures/Kontalk. This is a known issue but may not get resolved: Encrypt local media #951
Multiple devices are supported, go to the settings on an existing device and use the Maintenance->Register Device option.
Encryption:
OMEMO coming soon?
My verdict: So close!
I really like the concept of using XMPP protocol but with a client that can only communicate with the same client, so that you are sure your communication partner is also using a secure client app. However Kontalk unfortunately leaks data, so both sides are not totally secure. Also your phone number is how people add you as a contact so that compromises your privacy if you don't want people to know your phone number.
Communication types: Text, photo, video, audio, files, location, contacts
Country of origin: None
Source code: open
Encryption protocol: OpenPGP
Shared Secret exchange: ECDH P256
Message Encryption Cipher: AES-192
Business model: Free open source project, servers run by volunteers
Android app requires Google Play Services: No
Requires a phone number: Yes
Requires an email address: No
Your ID contains personal information: Phone
Data is locally encrypted: No
Encrypted by default: Yes
Perfect forward secrecy: Yes
Messages stored on server: Yes
Ephemeral messages: No
Puddle test: ?
Hammer test: Data recoverable Android client leaks files
Has contact verification: Yes
Leaks files: Android
Android app trackers (2): Google CrashLytics, Google Firebase Analytics
Websites: Java Client source, Android client source
Version tested: 4.1.5
Last tested: 6/22/2018
Notes:
Pros:
On F-Droid
Not dependent on Google play services
Cons:
People have to know your phone#
Android only
Android leaks files: found photos in Local Storage/Device Storage/Pictures/Kontalk. This is a known issue but may not get resolved: Encrypt local media #951
Multiple devices are supported, go to the settings on an existing device and use the Maintenance->Register Device option.
Encryption:
OMEMO coming soon?
My verdict: So close!
I really like the concept of using XMPP protocol but with a client that can only communicate with the same client, so that you are sure your communication partner is also using a secure client app. However Kontalk unfortunately leaks data, so both sides are not totally secure. Also your phone number is how people add you as a contact so that compromises your privacy if you don't want people to know your phone number.
Platforms: Android, iOS, Web
Communication types: Text, photos, group chat
Country of origin: UK
Source code: closed
Encryption protocol: ?
Shared Secret exchange: ?
Message Encryption Cipher: ?
Business model: ?
Android app requires Google Play Services: Yes
Requires a phone number: No
Requires an email address: No
Your ID contains personal information: No
Data is locally encrypted: ?
Encrypted by default: Yes
Perfect forward secrecy: ?
Messages stored on server: ?
Ephemeral messages: Yes
Puddle test: Data recoverable Messages are saved on their servers so you can access via the web login.
Hammer test: Data not recoverable When messages are deleted on all devices.
Has contact verification: No
Leaks files: No
Android app trackers (1): Google CrashLytics
Websites: Privacy Policy, Terms of Service
Version tested: Android: 1.1.79, iOS: 1.0.118
Last tested: 1/1/2021
Notes:
Update on 1/1/2021: There have been no updates to the application since it was reviewed in 2018 and no social media posts in 2 years so this product is essentially abandoned and doesn't look like it will get updates or bug fixes.
On Android new text messages are not displayed unless you exit the conversation then reenter it, even though on the other device it says the message has been read.
On Android there is a folder /device/SafeText/Images. While nothing appeared to be saved in this folder even after sending and receiving messages, it is concerning that this folder even exists. What is the purpose, will this ever be used? Will photos ever be leaked into this folder?
One nice feature is all chats automatically expire in 24 hours (or less if you set the expiration lower in settings). You can also delete any single message or the entire chat from both devices.
There is not much information on the website about how the application actually works, or which countries the servers are located in (the website just says outside of the USA in privacy friendly nations). However it is apparent that messages are saved on the server (until they expire) since I am able to log into the website portal and see all messages that were previously sent. Syncing between devices works very instantly and consistently.
To change devices simply download the app and login with your account credentials.
My verdict: Nice anonymity
I like that no personal information is required, and access to your contacts is optional. Messages also automatically expire in 24 hours or less.
There is a bug preventing messages from showing on Android, and there was a folder of concern I found but it did not appear to be used. Also legal jurisdiction (Cayman Islands is a territory of the UK) puts it very close to 5 eyes authorities. There is also very little documented technical information on the system architecture.
Communication types: Text, photos, group chat
Country of origin: UK
Source code: closed
Encryption protocol: ?
Shared Secret exchange: ?
Message Encryption Cipher: ?
Business model: ?
Android app requires Google Play Services: Yes
Requires a phone number: No
Requires an email address: No
Your ID contains personal information: No
Data is locally encrypted: ?
Encrypted by default: Yes
Perfect forward secrecy: ?
Messages stored on server: ?
Ephemeral messages: Yes
Puddle test: Data recoverable Messages are saved on their servers so you can access via the web login.
Hammer test: Data not recoverable When messages are deleted on all devices.
Has contact verification: No
Leaks files: No
Android app trackers (1): Google CrashLytics
Websites: Privacy Policy, Terms of Service
Version tested: Android: 1.1.79, iOS: 1.0.118
Last tested: 1/1/2021
Notes:
Update on 1/1/2021: There have been no updates to the application since it was reviewed in 2018 and no social media posts in 2 years so this product is essentially abandoned and doesn't look like it will get updates or bug fixes.
On Android new text messages are not displayed unless you exit the conversation then reenter it, even though on the other device it says the message has been read.
On Android there is a folder /device/SafeText/Images. While nothing appeared to be saved in this folder even after sending and receiving messages, it is concerning that this folder even exists. What is the purpose, will this ever be used? Will photos ever be leaked into this folder?
One nice feature is all chats automatically expire in 24 hours (or less if you set the expiration lower in settings). You can also delete any single message or the entire chat from both devices.
There is not much information on the website about how the application actually works, or which countries the servers are located in (the website just says outside of the USA in privacy friendly nations). However it is apparent that messages are saved on the server (until they expire) since I am able to log into the website portal and see all messages that were previously sent. Syncing between devices works very instantly and consistently.
To change devices simply download the app and login with your account credentials.
My verdict: Nice anonymity
I like that no personal information is required, and access to your contacts is optional. Messages also automatically expire in 24 hours or less.
There is a bug preventing messages from showing on Android, and there was a folder of concern I found but it did not appear to be used. Also legal jurisdiction (Cayman Islands is a territory of the UK) puts it very close to 5 eyes authorities. There is also very little documented technical information on the system architecture.
Platforms: Android, iOS (MacOS and Windows coming soon)
Communication types: Text, pictures, voice, video, files
Country of origin: China
Source code: closed
Encryption protocol: ?
Shared Secret exchange: ?
Message Encryption Cipher: AES-256
Business model: Who knows, it's China
Android app requires Google Play Services: Yes
Requires a phone number: No
Requires an email address: No
Your ID contains personal information: No
Data is locally encrypted: Yes
Encrypted by default: Yes
Perfect forward secrecy: Yes
Messages stored on server: Temporarily
Ephemeral messages: Yes
Puddle test: Data not recoverable Messages are saved on the device only.
Hammer test: Data not recoverable When messages are deleted on all devices.
Has contact verification: No
Leaks files: No
Android app trackers (1): Baidu Location
Websites:
Version tested: 6.0.10
Last tested: 8/25/2018
Notes:
**Caution!! This app is from a company based in China.
Trying to add a photo to the profile on Android just bring up a black screen with a spinning circle.
Private vault and cloud is a nice feature.
Everything seems to function just fine
My verdict: Do not download or use this app!
There is not a lot of information on the website about technical details, company info. This company is registered in Beijing. Without knowing more about the company I would stay away. China's recent technological spying on citizens makes any technology sourced from that country very suspect.
Communication types: Text, pictures, voice, video, files
Country of origin: China
Source code: closed
Encryption protocol: ?
Shared Secret exchange: ?
Message Encryption Cipher: AES-256
Business model: Who knows, it's China
Android app requires Google Play Services: Yes
Requires a phone number: No
Requires an email address: No
Your ID contains personal information: No
Data is locally encrypted: Yes
Encrypted by default: Yes
Perfect forward secrecy: Yes
Messages stored on server: Temporarily
Ephemeral messages: Yes
Puddle test: Data not recoverable Messages are saved on the device only.
Hammer test: Data not recoverable When messages are deleted on all devices.
Has contact verification: No
Leaks files: No
Android app trackers (1): Baidu Location
Websites:
Version tested: 6.0.10
Last tested: 8/25/2018
Notes:
**Caution!! This app is from a company based in China.
Trying to add a photo to the profile on Android just bring up a black screen with a spinning circle.
Private vault and cloud is a nice feature.
Everything seems to function just fine
My verdict: Do not download or use this app!
There is not a lot of information on the website about technical details, company info. This company is registered in Beijing. Without knowing more about the company I would stay away. China's recent technological spying on citizens makes any technology sourced from that country very suspect.
Platforms: Android, iOS
Communication types: Text, video chat, send EOS tokens
Country of origin: USA
Source code: closed
Encryption protocol: ?
Shared Secret exchange: ECDH P256
Message Encryption Cipher: ?
Business model: EOS token fees?
Android app requires Google Play Services: Yes
Requires a phone number: No
Requires an email address: No
Your ID contains personal information: No
Data is locally encrypted: Yes
Encrypted by default: Yes
Perfect forward secrecy: No
Messages stored on server: Temporarily
Ephemeral messages: No
Puddle test: Data not recoverable Messages are saved on the device only.
Hammer test: ?
Has contact verification: No
Leaks files: ?
Android app trackers (5): Branch, Google CrashLytics, Google Firebase Analytics, Instabug, OneSignal
Websites: Technical details
Version tested: 1.5.8
Last tested: 8/3/2019
Notes:
SenseChat is a messaging app the stores your public key on the blockchain that anyone can verify and use to send a message. Messages are sent peer to peer if possible, but if not they will be temporarily saved on a SenseChat server until they can be delivered.
When searching for contacts in the app you can type in any letter and get many results that match the first part of the user name to what you are searching. This seems like a privacy issue, but then again all public keys are stored on the public blockchain anyway, so there is no way to really keep all user identities of the service a secret.
The username you choose must be exactly 12 characters, I supposed to conform to requirements of the blockchain?
My verdict- Not mature and too many trackers
This app has fewer features than most other messaging apps. I also have concerns about the public nature of the blockchain and the ability to look up any and all user names that are registered in the system.
Communication types: Text, video chat, send EOS tokens
Country of origin: USA
Source code: closed
Encryption protocol: ?
Shared Secret exchange: ECDH P256
Message Encryption Cipher: ?
Business model: EOS token fees?
Android app requires Google Play Services: Yes
Requires a phone number: No
Requires an email address: No
Your ID contains personal information: No
Data is locally encrypted: Yes
Encrypted by default: Yes
Perfect forward secrecy: No
Messages stored on server: Temporarily
Ephemeral messages: No
Puddle test: Data not recoverable Messages are saved on the device only.
Hammer test: ?
Has contact verification: No
Leaks files: ?
Android app trackers (5): Branch, Google CrashLytics, Google Firebase Analytics, Instabug, OneSignal
Websites: Technical details
Version tested: 1.5.8
Last tested: 8/3/2019
Notes:
SenseChat is a messaging app the stores your public key on the blockchain that anyone can verify and use to send a message. Messages are sent peer to peer if possible, but if not they will be temporarily saved on a SenseChat server until they can be delivered.
When searching for contacts in the app you can type in any letter and get many results that match the first part of the user name to what you are searching. This seems like a privacy issue, but then again all public keys are stored on the public blockchain anyway, so there is no way to really keep all user identities of the service a secret.
The username you choose must be exactly 12 characters, I supposed to conform to requirements of the blockchain?
My verdict- Not mature and too many trackers
This app has fewer features than most other messaging apps. I also have concerns about the public nature of the blockchain and the ability to look up any and all user names that are registered in the system.
Platforms: Android, iOS
Communication types: Text, voice, images
Country of origin: USA
Source code: open
Encryption protocol: Crypto++
Shared Secret exchange: ECDH P521
Message Encryption Cipher: AES-256
Business model: Free open source project, Bitcoin donations
Android app requires Google Play Services: Yes
Requires a phone number: No
Requires an email address: No
Your ID contains personal information: No
Data is locally encrypted: Yes
Encrypted by default: Yes
Perfect forward secrecy: No
Messages stored on server: ?
Ephemeral messages: Yes
Puddle test: ?
Hammer test: Data recoverable Android client leaks files
Has contact verification: No
Leaks files: Android
Android app trackers (4): Google Analytics, Google Firebase Analytics, Google Tag Manager, uACRA
Websites: Source code, How SureSpot Works
Version tested: 72
Last tested: 1/24/2018
Notes:
Development seems to have ceased in May 2017. See this article which is very concerning: Developer’s Silence Raises Concern About Surespot Encrypted Messenger.
Data and threat analysis
Backup identity and save file to other location to be able to restore identity onto another device.
The app complains about needing Google Play services when opening, but it seems to work fine without it.
Video and audio are available by paid upgrade.
Individual chat messages can be deleted from all devices.
Android leaks files: found photos in Local Storage/Device Storage/Pictures/surespot
From Surespot Law Enforcement Guidelines
Surespot stores the following data on its servers:
From how surespot works
My verdict:
Definitely there are several concerns with this application (see linked article above). Some concerns are the lack of updates, amount of meta data stored on the server, and that the company is based in the US. Also the client leaks files on Android.
Communication types: Text, voice, images
Country of origin: USA
Source code: open
Encryption protocol: Crypto++
Shared Secret exchange: ECDH P521
Message Encryption Cipher: AES-256
Business model: Free open source project, Bitcoin donations
Android app requires Google Play Services: Yes
Requires a phone number: No
Requires an email address: No
Your ID contains personal information: No
Data is locally encrypted: Yes
Encrypted by default: Yes
Perfect forward secrecy: No
Messages stored on server: ?
Ephemeral messages: Yes
Puddle test: ?
Hammer test: Data recoverable Android client leaks files
Has contact verification: No
Leaks files: Android
Android app trackers (4): Google Analytics, Google Firebase Analytics, Google Tag Manager, uACRA
Websites: Source code, How SureSpot Works
Version tested: 72
Last tested: 1/24/2018
Notes:
Development seems to have ceased in May 2017. See this article which is very concerning: Developer’s Silence Raises Concern About Surespot Encrypted Messenger.
Data and threat analysis
Backup identity and save file to other location to be able to restore identity onto another device.
The app complains about needing Google Play services when opening, but it seems to work fine without it.
Video and audio are available by paid upgrade.
Individual chat messages can be deleted from all devices.
Android leaks files: found photos in Local Storage/Device Storage/Pictures/surespot
From Surespot Law Enforcement Guidelines
Surespot stores the following data on its servers:
- Usernames.
- Friend relationships (who is friends with who, blocked who, ignored who, deleted who).
- Conversation relationships (how many friends currently you have a "conversation" with - meaning have a sent or received a message with).
- Messages in the amount of MAX_MESSAGES_PER_USER (currently 1000) which each have a server timestamp, to username, from username, and encrypted content, or link to encrypted content (image or file).
- Encrypted message file data (image or other - anything but encrypted message content) is stored (encrypted in the same way text messages are) on rackspace cloud files.
- Total messages sent per user.
- Total images sent per user.
- Current message count per user. (How many messages they have stored in the database currently, will always be <= MAX_MESSAGES_PER_USER (currently 1000)).
- Signing (DSA) public keys and versions.
- Encryption (DH) public keys and versions.
- Encrypted "friend images" or avatars and friend aliases that are assigned to certain usernames. These are encrypted with a key generated from ECDH key derivation of assigning identity's private/public keypair.
- Google GCM id (used for push messaging) which is related to the username in the surespot database.
- Apple APN token (used for push messaging) which is related to the username in the surespot database.
- If voice messaging is purchased, a purchase token given to us by Google or Apple which is related to the username in the surespot database.
- Server logs may contain any of the above information and are in a 20 log - 5MB per log rotation.
From how surespot works
Sending a message
After two users invite then accept each other the users are now friends, the two friends can access each other's public keys, which allows key derivation and message exchange. The scenario plays out as follows at a high level glance:
alice wants to send bob a message
alice asks the server for the latest version of bob's public key
alice verifies bob's public key (which is signed by the bob and the server) against the hard coded server public key in the app, and also verifies the client signature using bob's previous key, then proceeds if valid
alice derives the shared secret
alice encrypts the message using AES 256bit GCM using the derived shared secret as the key and sends it to bob, the to and from key version used to generate the message are included as part of the message
bob receives the encrypted message
bob downloads and verifies the version of alice's public key needed to derive the shared secret for the message bob derives the (same) shared secret
bob decrypts the message using the shared secret
My verdict:
Definitely there are several concerns with this application (see linked article above). Some concerns are the lack of updates, amount of meta data stored on the server, and that the company is based in the US. Also the client leaks files on Android.
Platforms: Android, iOS, Windows, MacOS, Web
Communication types: Text, voice, file sharing
Country of origin: UK
Source code: partialopen
Encryption protocol: MProto
Shared Secret exchange: DH MODP2048
Message Encryption Cipher: AES-256
Business model: Self funded by Pavel Durov
Android app requires Google Play Services: Yes
Requires a phone number: Yes
Requires an email address: No
Your ID contains personal information: Optional aliases
Data is locally encrypted: No
Encrypted by default: No
Perfect forward secrecy: Yes
Messages stored on server: Yes
Ephemeral messages: Yes
Puddle test: Data recoverable Messages stored on the server.
Hammer test: Data recoverable Android app leaks files.
Has contact verification: Yes
Leaks files: Android
Android app trackers (2): Google Firebase Analytics, HockeyApp
Websites: Security
Version tested: 4.9.1
Last tested: 1/5/2019
Notes:
[Information provided by iteco]
There is a fork of Telegram on F-Droid (source code here) which claims to remove the dependency on Play Services and HockeySDK. This may be a better option for some people but this still uses the same custom crypto which is a main concern of mine. 0 trackers were found in the APK by Exodus.
Telegram channels are monitored by Telegram and government authorities. Telegram shuts down a public channel then Iran shuts off access to Telegram
The CEO of Telegram shows an unwillingness to consider that encrypting communications may actually preserve freedom of speech:
Encryption:
MTProto protocol: This is a roll-your-own protocol by Telegram (not a good idea). All traffic is encrypted by MTProto Part I encryption, but this is only between the client device and the server. Only secret chats are encrypted end to end using MTProto Part II.
Data storage:
On the CCA (in)security of MTProto
Jakob Jakobsen and Claudio Orlandi (Spring 2015)
https://eprint.iacr.org/2015/1177.pdf
Security Analysis of the Telegram IM
Tomas Susanka (January 2017)
https://www.susanka.eu/files/master-thesis-final.pdf
Security Analysis of Telegram
Hayk Saribekyan, Akaki Margvelashvili (May 2017)
https://courses.csail.mit.edu/6.857/2017/project/19.pdf
Link Previews:
Telegram provides previews (pictures, text) of website links that you send in messages. The app actively monitors what you type when writing a message and will send a request to the Telegram servers when it detects a URL has been typed. The Telegram servers pull data from the typed URL so that only the server IP is exposed, not your device IP. This been verified by myself by typing in the URL of this website in a Telgram chat and looking at the web server's access log files:
This feature is even available in Secret Chats. When I opened a new secret chat and typed in a URL I was prompted if I wanted to enable this feature:
So what this means is the link preview feature is available for use in Secret Chats, and so this would leak data to the Telegram server. It ALSO means that in Secret Chats the functionality that actively monitors what you type is fully functional. This is a concern because it might be possible to abuse this feature to monitor secret chats.
See this article for for information: Link previews in IM apps and privacy
My verdict: Too many problems with the protocol and data storage!
There are many issues with the protocol as shown by the referenced papers above. Rolling your own crypto is hard and MTProto has many problems.
Also all your phone contacts are stored on their servers, link previews get retrieved through the servers and non-secret chats are accessible to Telegram. Photos are stored in the system wide accessible local device storage even for secret chats.
Communication types: Text, voice, file sharing
Country of origin: UK
Source code: partialopen
Encryption protocol: MProto
Shared Secret exchange: DH MODP2048
Message Encryption Cipher: AES-256
Business model: Self funded by Pavel Durov
Android app requires Google Play Services: Yes
Requires a phone number: Yes
Requires an email address: No
Your ID contains personal information: Optional aliases
Data is locally encrypted: No
Encrypted by default: No
Perfect forward secrecy: Yes
Messages stored on server: Yes
Ephemeral messages: Yes
Puddle test: Data recoverable Messages stored on the server.
Hammer test: Data recoverable Android app leaks files.
Has contact verification: Yes
Leaks files: Android
Android app trackers (2): Google Firebase Analytics, HockeyApp
Websites: Security
Version tested: 4.9.1
Last tested: 1/5/2019
Notes:
[Information provided by iteco]
There is a fork of Telegram on F-Droid (source code here) which claims to remove the dependency on Play Services and HockeySDK. This may be a better option for some people but this still uses the same custom crypto which is a main concern of mine. 0 trackers were found in the APK by Exodus.
Telegram channels are monitored by Telegram and government authorities. Telegram shuts down a public channel then Iran shuts off access to Telegram
The CEO of Telegram shows an unwillingness to consider that encrypting communications may actually preserve freedom of speech:

Encryption:
MTProto protocol: This is a roll-your-own protocol by Telegram (not a good idea). All traffic is encrypted by MTProto Part I encryption, but this is only between the client device and the server. Only secret chats are encrypted end to end using MTProto Part II.
- Keys are negotiated using Diffie-Hellman exchange, keys are recreated when 100 messages have been exchanged or one week has elapsed.
- A shared key is generated from the negotiated key pairs
- A message key is created using part of the hash of the shared key combined with 32 bytes from the shared key
- An AES key and initialization vector are created using hashes of combinations of the shared key and message key
- The AES key and initialization vector are used to encrypt the message
- The message key, encrypted data and the last 64 bits of the shared key's SHA1 hash are sent to the recipient
Data storage:
- Telegram stores regular cloud chats encrypted on their servers but they control all the encryption keys.
- All your contacts' phone numbers and names are stored on their servers.
- Android leaks files: found photos in Local Storage/Device Storage/Android/data/org.telegram.messenger. When you log out of Telegram it says that it will kill all your secret chats, however the photos remain saved on the device.
On the CCA (in)security of MTProto
Jakob Jakobsen and Claudio Orlandi (Spring 2015)
https://eprint.iacr.org/2015/1177.pdf
Security Analysis of the Telegram IM
Tomas Susanka (January 2017)
https://www.susanka.eu/files/master-thesis-final.pdf
Security Analysis of Telegram
Hayk Saribekyan, Akaki Margvelashvili (May 2017)
https://courses.csail.mit.edu/6.857/2017/project/19.pdf
Link Previews:
Telegram provides previews (pictures, text) of website links that you send in messages. The app actively monitors what you type when writing a message and will send a request to the Telegram servers when it detects a URL has been typed. The Telegram servers pull data from the typed URL so that only the server IP is exposed, not your device IP. This been verified by myself by typing in the URL of this website in a Telgram chat and looking at the web server's access log files:
149.154.161.8 - - [05/Jan/2019:19:48:44 -0500] "GET / HTTP/1.1" 200 21112 "-" "TelegramBot (like TwitterBot)"I paused a few times as I was typing and so several URLs were retrieved.
149.154.161.17 - - [05/Jan/2019:19:49:41 -0500] "GET /test HTTP/1.1" 404 202 "-" "TelegramBot (like TwitterBot)"
149.154.161.12 - - [05/Jan/2019:19:50:04 -0500] "GET /testq HTTP/1.1" 404 203 "-" "TelegramBot (like TwitterBot)"
149.154.161.12 - - [05/Jan/2019:19:50:13 -0500] "GET /testqfghfd HTTP/1.1" 404 208 "-" "TelegramBot (like TwitterBot)"
This feature is even available in Secret Chats. When I opened a new secret chat and typed in a URL I was prompted if I wanted to enable this feature:

So what this means is the link preview feature is available for use in Secret Chats, and so this would leak data to the Telegram server. It ALSO means that in Secret Chats the functionality that actively monitors what you type is fully functional. This is a concern because it might be possible to abuse this feature to monitor secret chats.
See this article for for information: Link previews in IM apps and privacy
[Information provided by JR]
Metadata leakage:
- When you are online or not or whether the application is running or not is publicly viewable.
- Who you talk to, when, and the precise time you send a message, and how frequently is publicly viewable via commandline tools.
- If an attacker knows your phone number, the attacker will be able to silently log your Telegram activity without you knowing about it or being informed they have you as a contact.
Stalking via Telegram through the use of Commandline Tools (Flisback, Ola, updated 2015, December 16th)
https://oflisback.github.io/telegram-stalking/
Contact Theft through Telegram, Paragraph 9 and 10.
"Operational Telegram" "The Grugq (assumed name" (Posted November 18th, 2015)
https://medium.com/@thegrugq/operational-telegram-cbbaadb9013a#.a62knhv8x
A practical Analysis of the Telegram Messaging Protocol
Jakobsen, Jakob B. (Published September 2015)
http://cs.au.dk/~jakjak/master-thesis.pdf
My verdict: Too many problems with the protocol and data storage!
There are many issues with the protocol as shown by the referenced papers above. Rolling your own crypto is hard and MTProto has many problems.
Also all your phone contacts are stored on their servers, link previews get retrieved through the servers and non-secret chats are accessible to Telegram. Photos are stored in the system wide accessible local device storage even for secret chats.
Platforms: Android, iOS
Communication types: Text, group chat, photos, videos, audio
Country of origin: Canada
Source code: closed
Encryption protocol: ?
Shared Secret exchange: ?
Message Encryption Cipher: ?
Business model: ?
Android app requires Google Play Services: Yes
Requires a phone number: Either
Requires an email address: Either
Your ID contains personal information: No
Data is locally encrypted: ?
Encrypted by default: ?
Perfect forward secrecy: ?
Messages stored on server: ?
Ephemeral messages: Yes
Puddle test: ?
Hammer test: ?
Has contact verification: ?
Leaks files: ?
Android app trackers (0): None
Websites:
Version tested: 1.1.6
Last tested: 8/26/2018
Notes:
Spelling and punctuation errors make this program very unprofessional.
The avatar would not save when creating my profile.
Twicie crashed in Android when trying to send an invitation when it did not have permisions to access the contacts. I would rather type in a search name than give an app complete access to my contacts. iPhone app simply showed an empty list.
My verdict: Unusable
We could not even get connected to start a chat and test. Way too many issues and bugs in this app.
Communication types: Text, group chat, photos, videos, audio
Country of origin: Canada
Source code: closed
Encryption protocol: ?
Shared Secret exchange: ?
Message Encryption Cipher: ?
Business model: ?
Android app requires Google Play Services: Yes
Requires a phone number: Either
Requires an email address: Either
Your ID contains personal information: No
Data is locally encrypted: ?
Encrypted by default: ?
Perfect forward secrecy: ?
Messages stored on server: ?
Ephemeral messages: Yes
Puddle test: ?
Hammer test: ?
Has contact verification: ?
Leaks files: ?
Android app trackers (0): None
Websites:
Version tested: 1.1.6
Last tested: 8/26/2018
Notes:
Spelling and punctuation errors make this program very unprofessional.
The avatar would not save when creating my profile.
Twicie crashed in Android when trying to send an invitation when it did not have permisions to access the contacts. I would rather type in a search name than give an app complete access to my contacts. iPhone app simply showed an empty list.
My verdict: Unusable
We could not even get connected to start a chat and test. Way too many issues and bugs in this app.
Platforms: Android, iOS
Communication types: text, photos, video and audio calls
Country of origin: Canada
Source code: closed
Encryption protocol: Vanish
Shared Secret exchange: ?
Message Encryption Cipher: ?
Business model: ?
Android app requires Google Play Services: Yes
Requires a phone number: No
Requires an email address: No
Your ID contains personal information: No
Data is locally encrypted: Yes
Encrypted by default: Yes
Perfect forward secrecy: ?
Messages stored on server: ?
Ephemeral messages: No
Puddle test: Data not recoverable The encryption keys are only stored on your device.
Hammer test: Data not recoverable When messages are deleted on all devices.
Has contact verification: No
Leaks files: No
Android app trackers (2): Google CrashLytics, Google Firebase Analytics
Websites: Preliminary audit
Version tested: 2.04 (Android), 2.1 (iOS)
Last tested: 7/11/2018
Notes:
Attempting to backup the identity on iOS results in an error that it is "Unable to export data"
If you take a screenshot there is a note posted in the chat.
On iOS there is no preview of photos sent or received, you must touch on the link to view the photo. However there is a preview in the Android app. Decryption the first time on iOS seems to take a while. Accessing the photo again is quick.
On iOS there is the option to setup your fingerprint authentication to open the application
When testing with "C" on iOS, his app crashed and locked him out for some time with the spinning circle of death. After a reboot and waiting a little while he was able to log back in, then the app would not accept his password.
On Android some buttons do not respond well and need some extended touching to activate. To enter a chat I had to click on the notification, pressing on the chat entry in the app does nothing. Swiping between the main screen sections of Contacts, Chats and Settings is not obvious at first and touching each heading does not move to that section.
I received the error "connect_to_internet_prompt_title connect_to_internet_prompt" when I lost internet connectivity while moving around. Seems like a template of error messages has not been update with relavent error message text.
Encryption:
No details except it is "Patent Pending".
My verdict: Not ready yet.
There are many bugs and outright broken things in the apps on both platforms that make them painful to use. The security on the backend seems to be adequate with what little information I could get from the website, but there needs to be more documentation, FAQs and details on the encryption used. Much needs to be improved before I would even consider this worthy of trying.
Communication types: text, photos, video and audio calls
Country of origin: Canada
Source code: closed
Encryption protocol: Vanish
Shared Secret exchange: ?
Message Encryption Cipher: ?
Business model: ?
Android app requires Google Play Services: Yes
Requires a phone number: No
Requires an email address: No
Your ID contains personal information: No
Data is locally encrypted: Yes
Encrypted by default: Yes
Perfect forward secrecy: ?
Messages stored on server: ?
Ephemeral messages: No
Puddle test: Data not recoverable The encryption keys are only stored on your device.
Hammer test: Data not recoverable When messages are deleted on all devices.
Has contact verification: No
Leaks files: No
Android app trackers (2): Google CrashLytics, Google Firebase Analytics
Websites: Preliminary audit
Version tested: 2.04 (Android), 2.1 (iOS)
Last tested: 7/11/2018
Notes:
Attempting to backup the identity on iOS results in an error that it is "Unable to export data"
If you take a screenshot there is a note posted in the chat.
On iOS there is no preview of photos sent or received, you must touch on the link to view the photo. However there is a preview in the Android app. Decryption the first time on iOS seems to take a while. Accessing the photo again is quick.
On iOS there is the option to setup your fingerprint authentication to open the application
When testing with "C" on iOS, his app crashed and locked him out for some time with the spinning circle of death. After a reboot and waiting a little while he was able to log back in, then the app would not accept his password.
On Android some buttons do not respond well and need some extended touching to activate. To enter a chat I had to click on the notification, pressing on the chat entry in the app does nothing. Swiping between the main screen sections of Contacts, Chats and Settings is not obvious at first and touching each heading does not move to that section.
I received the error "connect_to_internet_prompt_title connect_to_internet_prompt" when I lost internet connectivity while moving around. Seems like a template of error messages has not been update with relavent error message text.
Encryption:
No details except it is "Patent Pending".
My verdict: Not ready yet.
There are many bugs and outright broken things in the apps on both platforms that make them painful to use. The security on the backend seems to be adequate with what little information I could get from the website, but there needs to be more documentation, FAQs and details on the encryption used. Much needs to be improved before I would even consider this worthy of trying.
Platforms: Android, iOS
Communication types: Text, group chat, voice calls, video chat, files, contact, location
Country of origin: Belgium
Source code: closed
Encryption protocol: ?
Shared Secret exchange: DH MODP1536
Message Encryption Cipher: AES-128
Business model: Enterprise version of the platform
Android app requires Google Play Services: Yes
Requires a phone number: Yes
Requires an email address: No
Your ID contains personal information: Phone
Data is locally encrypted: Yes
Encrypted by default: Yes
Perfect forward secrecy: Yes
Messages stored on server: Temporarily
Ephemeral messages: Yes
Puddle test: Data not recoverable Messages are saved on the device only.
Hammer test: Data recoverable Android app leaks files.
Has contact verification: No
Leaks files: Android
Android app trackers (2): Google CrashLytics, Google Firebase Analytics
Websites: Whitepaper
Version tested: 1.3.7 (iOS), 1.4.0 (Android)
Last tested: 3/9/2019
Notes:
Access to contacts is essentially required- On iOS I could not add a new contact by manually adding a phone number. On Android I was able to start a new chat and manually type in a phone number. I could not add the contact to the app's contact list on either app
When I first made contact from my Android to iPhone it kept generating new keys. Although throughout the messaging test period I noticed every once in a while it would show a message on iOS that new keys had been generated, so maybe this is how it provides perfect forward secrecy. I did not see these messages on the Android.
The app does have ephemeral messages that can be set to expire from 5 minutes to 5 days. Unfortunately setting the timer only applies to the that message sent, it then reverts back to no timeout for the next message. There is no default ephemeral timeout setting.
On the Android device all pictures sent and received were saved unencrypted in /Android/data/com.accelior.vega/files/Pictures
My Verdict: Not private enough
The app worked well, however major concerns are the use of your phone number as your identifier and a requirement to give access to your phone's contacts list. The app also saves files unencrypted in public storage for any app to access. If you want to use your phone number other apps like Signal are more private and secure.
Communication types: Text, group chat, voice calls, video chat, files, contact, location
Country of origin: Belgium
Source code: closed
Encryption protocol: ?
Shared Secret exchange: DH MODP1536
Message Encryption Cipher: AES-128
Business model: Enterprise version of the platform
Android app requires Google Play Services: Yes
Requires a phone number: Yes
Requires an email address: No
Your ID contains personal information: Phone
Data is locally encrypted: Yes
Encrypted by default: Yes
Perfect forward secrecy: Yes
Messages stored on server: Temporarily
Ephemeral messages: Yes
Puddle test: Data not recoverable Messages are saved on the device only.
Hammer test: Data recoverable Android app leaks files.
Has contact verification: No
Leaks files: Android
Android app trackers (2): Google CrashLytics, Google Firebase Analytics
Websites: Whitepaper
Version tested: 1.3.7 (iOS), 1.4.0 (Android)
Last tested: 3/9/2019
Notes:
Access to contacts is essentially required- On iOS I could not add a new contact by manually adding a phone number. On Android I was able to start a new chat and manually type in a phone number. I could not add the contact to the app's contact list on either app
When I first made contact from my Android to iPhone it kept generating new keys. Although throughout the messaging test period I noticed every once in a while it would show a message on iOS that new keys had been generated, so maybe this is how it provides perfect forward secrecy. I did not see these messages on the Android.
The app does have ephemeral messages that can be set to expire from 5 minutes to 5 days. Unfortunately setting the timer only applies to the that message sent, it then reverts back to no timeout for the next message. There is no default ephemeral timeout setting.
On the Android device all pictures sent and received were saved unencrypted in /Android/data/com.accelior.vega/files/Pictures
My Verdict: Not private enough
The app worked well, however major concerns are the use of your phone number as your identifier and a requirement to give access to your phone's contacts list. The app also saves files unencrypted in public storage for any app to access. If you want to use your phone number other apps like Signal are more private and secure.
Platforms: Android, iOS, MacOS, Windows, Linux
Communication types: Text, group messaging, voice and video calls, photos
Country of origin: Japan
Source code: closed
Encryption protocol: ?
Shared Secret exchange: ECDH25519
Message Encryption Cipher: Salsa20
Business model: VoIP calling plans
Android app requires Google Play Services: Yes
Requires a phone number: Yes
Requires an email address: No
Your ID contains personal information: Phone
Data is locally encrypted: No
Encrypted by default: Yes
Perfect forward secrecy: Yes
Messages stored on server: Temporarily
Ephemeral messages: Yes
Puddle test: Data not recoverable Messages are saved on the device only.
Hammer test: Data recoverable Android app leaks files.
Has contact verification: Yes
Leaks files: Android
Android app trackers (9): Adjust, App Nexus, Apptimize, Braze, Google Ads, Google CrashLytics, Google DoubleClick, Google Firebase Analytics, MixPanel
Websites: Support, Security Overview, <a href="https://www.viber.com/app/uploads/viber-encryption-overview.pdf>Encryption Overview</a>
Version tested: 8.6.0
Last tested: 4/3/2018
Notes:
Requires a phone number to register, add contacts using their phone number.
Custom protocol- from the security overview:
Android Trojan Steals Data From Facebook Messenger, Skype, Other IM Clients
My Verdict:
Do not use this application since it leaks message data.
Communication types: Text, group messaging, voice and video calls, photos
Country of origin: Japan
Source code: closed
Encryption protocol: ?
Shared Secret exchange: ECDH25519
Message Encryption Cipher: Salsa20
Business model: VoIP calling plans
Android app requires Google Play Services: Yes
Requires a phone number: Yes
Requires an email address: No
Your ID contains personal information: Phone
Data is locally encrypted: No
Encrypted by default: Yes
Perfect forward secrecy: Yes
Messages stored on server: Temporarily
Ephemeral messages: Yes
Puddle test: Data not recoverable Messages are saved on the device only.
Hammer test: Data recoverable Android app leaks files.
Has contact verification: Yes
Leaks files: Android
Android app trackers (9): Adjust, App Nexus, Apptimize, Braze, Google Ads, Google CrashLytics, Google DoubleClick, Google Firebase Analytics, MixPanel
Websites: Support, Security Overview, <a href="https://www.viber.com/app/uploads/viber-encryption-overview.pdf>Encryption Overview</a>
Version tested: 8.6.0
Last tested: 4/3/2018
Notes:
Requires a phone number to register, add contacts using their phone number.
Custom protocol- from the security overview:
Viber’s protocol uses the same concepts of the “double ratchet” protocol used in Open Whisper Systems Signal application, however, Viber’s implementation was developed from scratch and does not share Signal’s source code.The application is very functional, and video calling quality is very clear. Unfortunately files are saved unencrypted on the data partition exposing pictures and possibly other data files. For example, /Android/data/com.viber.voip/files/.thumbnails
Android Trojan Steals Data From Facebook Messenger, Skype, Other IM Clients
My Verdict:
Do not use this application since it leaks message data.
Platforms: Android, iOS, MacOS, Windows, Linux
Communication types: Text, files, photos, video, location, contacts, audio
Country of origin: UK
Source code: closed
Encryption protocol: ?
Shared Secret exchange: RSA 3072 PKI
Message Encryption Cipher: AES-256
Business model: Subscription plans for premium features
Android app requires Google Play Services: No
Requires a phone number: Either
Requires an email address: Either
Your ID contains personal information: No
Data is locally encrypted: No
Encrypted by default: Yes
Perfect forward secrecy: Yes
Messages stored on server: Yes
Ephemeral messages: No
Puddle test: Data recoverable Messages are stored on the server.
Hammer test: Data recoverable Android app leaks files.
Has contact verification: No
Leaks files: Android
Android app trackers (2): Google CrashLytics, Google Firebase Analytics
Websites: Encryption
Version tested: 1.8.73
Last tested: 1/28/2018
Notes:
This is a very nice multi-device application that will sync your content across all devices. There are several tiers of features for use by individuals, teams or enterprises. The individual free tier is very nice, unfortunately it is missing locally encrypted database and sent message editing. The $5.99/month package adds these features.
Also included are online saving of notes, passwords, files and a calendar.
Transferring to another Android device: just download the app and login with your account username, password and secret phrase.
Android leaks files: found photos in Local Storage/Device Storage/Android/data/com.vipole.client/cache
My verdict:
This is a nice application, but you must pay a monthly fee to get local encryption at rest and deletion of messages.
Communication types: Text, files, photos, video, location, contacts, audio
Country of origin: UK
Source code: closed
Encryption protocol: ?
Shared Secret exchange: RSA 3072 PKI
Message Encryption Cipher: AES-256
Business model: Subscription plans for premium features
Android app requires Google Play Services: No
Requires a phone number: Either
Requires an email address: Either
Your ID contains personal information: No
Data is locally encrypted: No
Encrypted by default: Yes
Perfect forward secrecy: Yes
Messages stored on server: Yes
Ephemeral messages: No
Puddle test: Data recoverable Messages are stored on the server.
Hammer test: Data recoverable Android app leaks files.
Has contact verification: No
Leaks files: Android
Android app trackers (2): Google CrashLytics, Google Firebase Analytics
Websites: Encryption
Version tested: 1.8.73
Last tested: 1/28/2018
Notes:
This is a very nice multi-device application that will sync your content across all devices. There are several tiers of features for use by individuals, teams or enterprises. The individual free tier is very nice, unfortunately it is missing locally encrypted database and sent message editing. The $5.99/month package adds these features.
Also included are online saving of notes, passwords, files and a calendar.
Transferring to another Android device: just download the app and login with your account username, password and secret phrase.
Android leaks files: found photos in Local Storage/Device Storage/Android/data/com.vipole.client/cache
My verdict:
This is a nice application, but you must pay a monthly fee to get local encryption at rest and deletion of messages.
Platforms: Android, iOS, MacOS, Windows, Linux
Communication types: Text, files, photos, video, location, contacts, audio
Country of origin: UK
Source code: closed
Encryption protocol: ?
Shared Secret exchange: RSA 3072 PKI
Message Encryption Cipher: AES-256
Business model: Enterprise version of the platform
Android app requires Google Play Services: No
Requires a phone number: Either
Requires an email address: Either
Your ID contains personal information: No
Data is locally encrypted: Yes
Encrypted by default: Yes
Perfect forward secrecy: Yes
Messages stored on server: Yes
Ephemeral messages: Yes
Puddle test: Data recoverable Messages are stored on the server.
Hammer test: Data recoverable Android app leaks files.
Has contact verification: No
Leaks files: Android
Android app trackers (2): Google CrashLytics, Google Firebase Analytics
Websites: Encryption
Version tested: 1.8.73
Last tested: 1/28/2018
Notes:
This is a very nice multi-device application that will sync your content across all devices. There are several tiers of features for use by individuals, teams or enterprises. The individual free tier is very nice, unfortunately it is missing locally encrypted database and sent message editing. The $5.99/month package adds these features.
Also included are online saving of notes, passwords, files and a calendar.
Transferring to another Android device: just download the app and login with your account username, password and secret phrase.
Android leaks files: found photos in Local Storage/Device Storage/Android/data/com.vipole.client/cache
My verdict:
This is a nice application, but you must pay a monthly fee to get local encryption at rest and deletion of messages.
Communication types: Text, files, photos, video, location, contacts, audio
Country of origin: UK
Source code: closed
Encryption protocol: ?
Shared Secret exchange: RSA 3072 PKI
Message Encryption Cipher: AES-256
Business model: Enterprise version of the platform
Android app requires Google Play Services: No
Requires a phone number: Either
Requires an email address: Either
Your ID contains personal information: No
Data is locally encrypted: Yes
Encrypted by default: Yes
Perfect forward secrecy: Yes
Messages stored on server: Yes
Ephemeral messages: Yes
Puddle test: Data recoverable Messages are stored on the server.
Hammer test: Data recoverable Android app leaks files.
Has contact verification: No
Leaks files: Android
Android app trackers (2): Google CrashLytics, Google Firebase Analytics
Websites: Encryption
Version tested: 1.8.73
Last tested: 1/28/2018
Notes:
This is a very nice multi-device application that will sync your content across all devices. There are several tiers of features for use by individuals, teams or enterprises. The individual free tier is very nice, unfortunately it is missing locally encrypted database and sent message editing. The $5.99/month package adds these features.
Also included are online saving of notes, passwords, files and a calendar.
Transferring to another Android device: just download the app and login with your account username, password and secret phrase.
Android leaks files: found photos in Local Storage/Device Storage/Android/data/com.vipole.client/cache
My verdict:
This is a nice application, but you must pay a monthly fee to get local encryption at rest and deletion of messages.